3,844 views
 HaXx.Me #3 – Corelan Team documentation
HaXx.Me #3 – Corelan Team documentation
Last week (oct 17 2010), Lincoln (one of the Corelan Team members) informed the other team members about an ongoing hacking challenge (HaXx.Me #03) organized and hosted by MaXe (@intern0t).
When I saw his message, it was already Sunday night and I knew I had to get up early the next day. Nevertheless I chose to have a bit of fun before going to sleep.
So let the fun begin…
The target
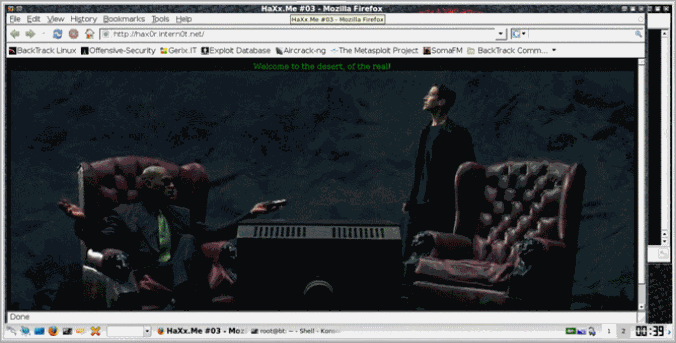
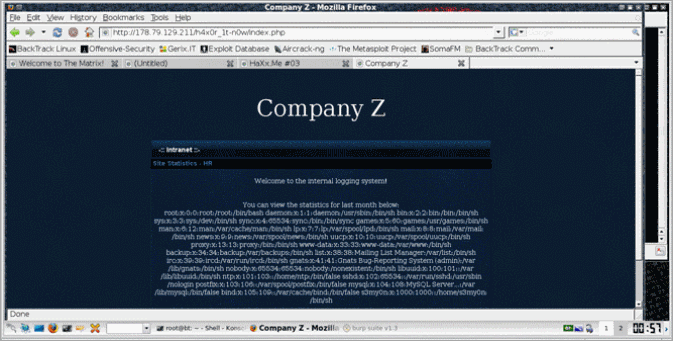
Let’s browse the target http://hax0r.intern0t.net/
Ok… After few seconds looking around and trying to spot any hint in the picture I decided it’s time to see if the source can tell something useful.
with version information in the chaos domain can reveal your next step. Services, services, services –>
A quick search on Google revealed the following interesting OSVDB entry : http://osvdb.org/23.
OK, let’s try on our target:
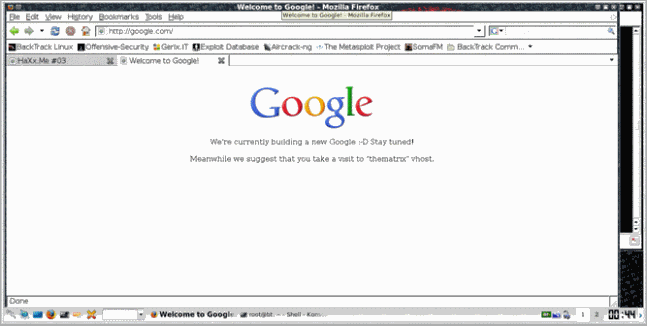
root@bt:~# nslookup -q=txt -class=chaos version.bind hax0r.intern0t.net Server: hax0r.intern0t.net Address: 178.79.129.211#53 version.bind text = "So you finally figured it out.. You need to use me as a nameserver and then browse to google.com in order to continue your journey."
I followed the advice and got this page:
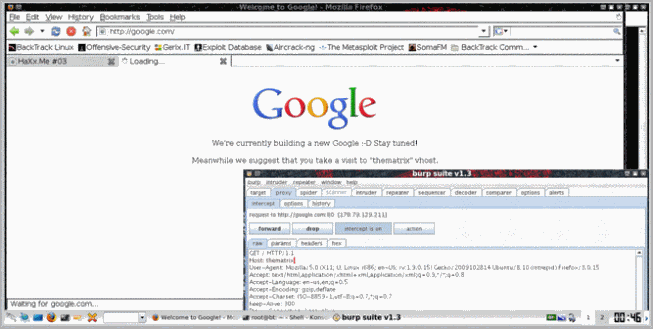
Whoa, very interesting… Few more attempts, then time to bed. The challenge must wait until the next day. The next day Fancy joined us and we figured out we need to play with http requests so we used Burp to intercept them…
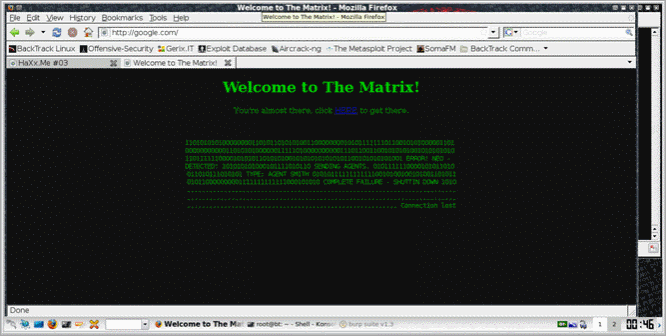
After changing the host parameter, we got this :
The link led us to http://178.79.129.211/h4x0r_1t-n0w/ :
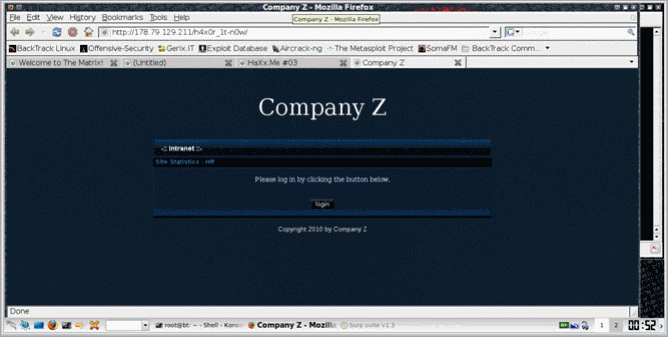
The real target
Oops, not that easy :P… We had to bypass the login page. A quick look at the source code gave us another hint:
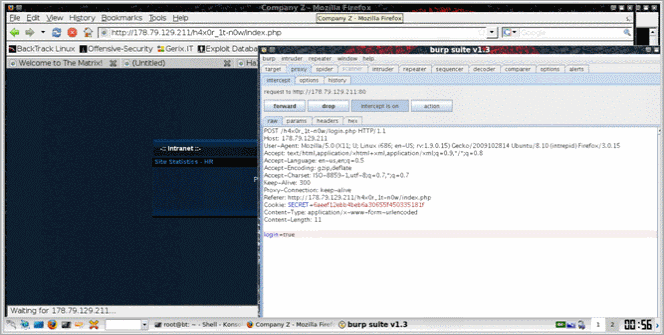
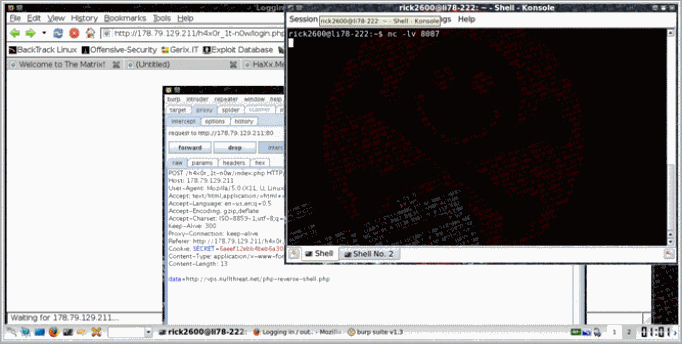
So, we grabbed the source.tar. With the source code in our hands we tried to bypass the login page. We used burp suite again to intercept our request and see how data is being transmitted…
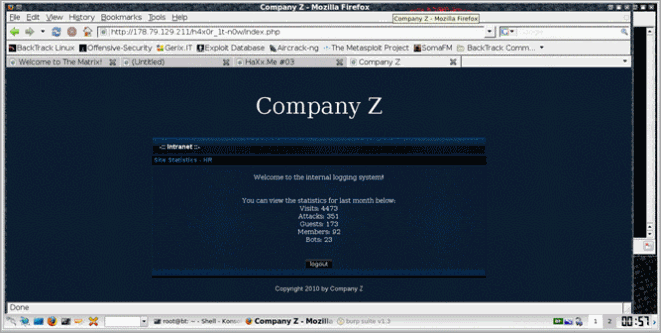
Hey wait! What happens if we change the login=false to login=true ? :P
Bingo!!! Successfully logged in!!! :D
Now how could we make it more useful?
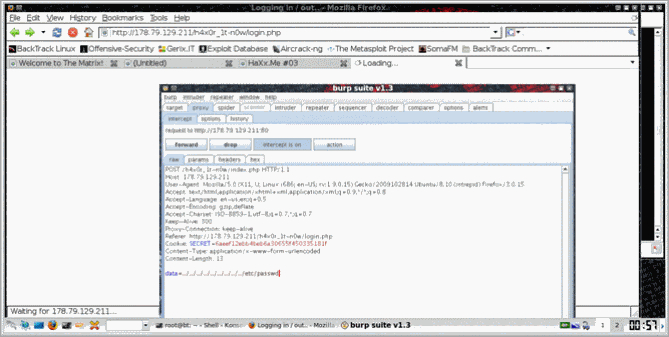
Going back to request there was another parameter "data" and changing it a bit we could see that it was vulnerable to LFI and playing a bit with param we discovered that it was vulnerable to RFI too. This means even more fun :D
0wned
Time to get a shell…
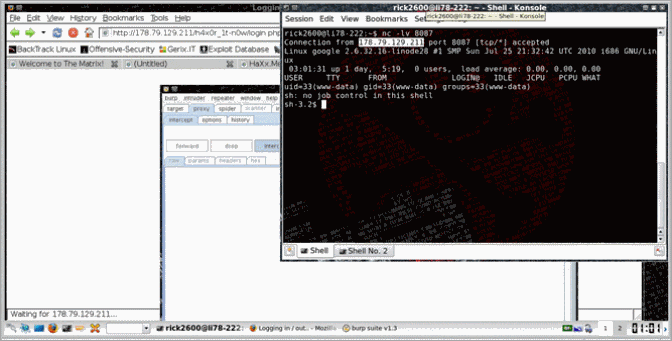
Thanks to Nullthreat for providing the php reverse shell. We set up a listener, included it in the data parameter and wondered if the shell will show up.
Forwarding the request….
Woot… we are in :D
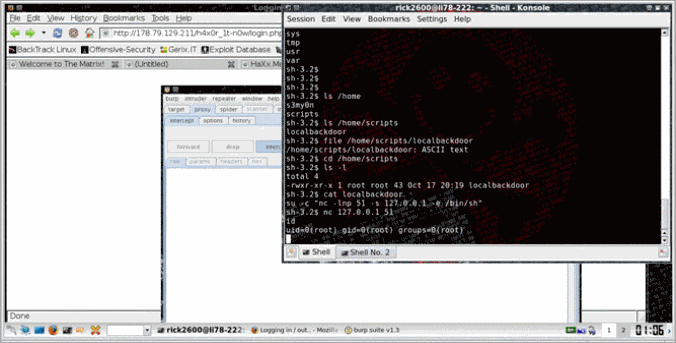
The next step is to find the key, obviously we didn’t have permission to read the file, so poking around a bit we found a file called localbackdoor in /home/scripts, it was a listener to port 51 owned by root.
Connecting…
Boom.. root :D
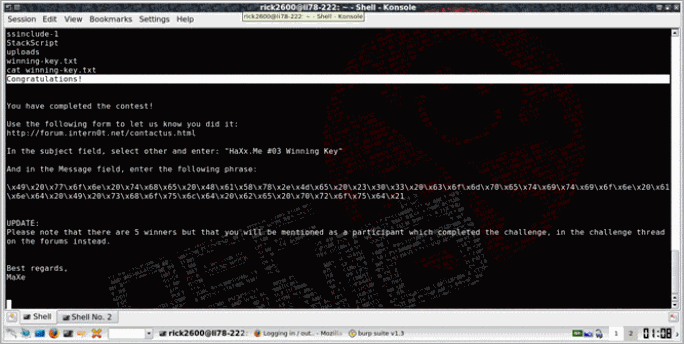
So let’s read the key and complete the challenge…
The message says: I won the HaXx.Me #03 competition and I should be proud!
Video
nullthreat made a nice video about the steps Corelan Team took to complete the challenge :
or click this link
A documentation video, made by intern0t, can be found here : http://intern0t.blip.tv/
Conclusion & Thanks to
Nice wargame, good exercise & congrats to the winners of the challenge !
Thanks to :
- MaXe for providing the challenge
- Corelan Team for working together to complete the challenge
 Copyright secured by Digiprove © 2010 Peter Van Eeckhoutte
Copyright secured by Digiprove © 2010 Peter Van Eeckhoutte
© 2010 – 2021, Corelan Team (rick2600). All rights reserved.