1,165 views
 HITB2014AMS – Day 1 – Keynote 2: Building a Strategic Defense Against the Global Threat Landscape
HITB2014AMS – Day 1 – Keynote 2: Building a Strategic Defense Against the Global Threat Landscape
Kristin starts her keynote by explaining that she has been in the business about 22 years ago and used to be in public services. A long time ago, she married a husband who was in the military and ran a program for spouses to meet/connect while their husbands were deployed. During one of the meetings, they discovered “FTP”, which allowed them to write letters and send them to the marines. She was intrigued and started learning how TCP/IP works, and helped connecting systems. At a later stage, she got involved with connecting routers and implementing access lists… that was 23 years ago.Later, she joined TrueSecure (which became CyberTrust, later Verizon) and became a pentester/ethical hacker. Even today, she still uses her iPad to show CISO’s if it’s still possible to get inside networks and convince them that things may not be as secure as they think it is.

IBM runs the IT environment for thousands of customers, Kristin explains. That also means that they have seen every single type of security incident possible, which allowed her to learn a lot and draw important lessons.
As a CISO, you should learn how ot use small worlds and be humble. Speaking to executives is like speaking to babies, which is also why women make great CISO’s, Kristin continues.
Lesson 1: You can’t stop the business from innovating.
To be succesful at security, you need to understand your audience. The security world is being shaped by a few dynamics: Globalization, Internet enabled mobile devices, the Internet of Things, Analytics and Cloud computing a just a few examples of these dynamics, driven by an increasing desire and need to be mobile.

Businesses need to be mobile, explore new geographical markets and areas, or open production facilities in countries that have a lower labor cost . Businesses need to act in a global fashion and, as a result, use mobile applications and tools to attact customers and to support business growth. Unfortunately, these applications are not built by the Security dept, but by the Marketing Officer. Kristin even expects the IT budgets for marketing departments to increase and thus their influence will also increase. Guess what, who’s writing the apps? Right, “cousin Chuck” has experience with writing apps for iTunes, let’s ask him. And will it be written with security in mind? The cloud makes it possible to deploy new applications and delivery of new business services. The reality is that businesses need to interact with “new consumers”, using new technology. You can’t stop that.
Kristin states “for me, the biggest unknown is regulation”. All of the aforementioned is subject to radical change if the right to anonymity is instantiated.
Lesson 2: Like any biological system, we are all infected.
In a room with 300 people/executives, at least 30 people have been compromised. In most cases, people don’t believe that. People forget that “anything that is connected to the Internet can be hacked”. At the same time, we are connecting “Everything” to the internet. The internet of things is a reality, and there’s a fair possibility that much of it has been compromised already. At the same time, only 1 out of 100 security compromises are ever detected. The IBM CyberSecurity Intelligence Team estimates that about 3% of all incidents analyzed by IBM Response Services could be considered “noteworthy” ( = potentially material of significant impact). An average organization (of 15K employees), she continues, sees about 1.7 million probes per week, both internally and externally. Of course, not all of these probes are malicious. About 324 of them represent actual attacks, but without proper tools to detect and manage this, it’s extremely difficult to detect these attacks. Isolating attacks from noise is important and, at the same time, extremely difficult.
About 56% of the attacks come from outsiders, 17% is caused by malicious insiders, Kristin says. A majority of the 17% insiders are privileged users (administrators, etc). IT people typically don’t like to work within the security boundaries and structures. The people that do the most harm from the inside, are “hard-wired” to do the harm, with high privileges.
Lesson 3: The “Bad Guys” rely on our stupidity, ignorance, or just plain dumb mistakes to get in.
People will click stuff. They will double-click stuff. But it’s not the only reason why hackers get in. Companies use vulnerable software, fail to install patches, use AV. They fail to report lost/stolen devices, allow people to connect their devices to insecure networks (WiFI hotspot at Starbucks), use weak passwords or share business passwords for general use, give passwords over the phone etc etc. From an infrastructure point of view, systems are not hardened the way they should be. Test systems are connected to the Internet with default configuration & settings; patches are not deployed on a regular/timing basis; networks are not segmented, no tools are in place to detect incidents, legacy software/OSes are still being used in a lot of places.
Lesson 4: Getting ahead of the threat requires you to know how to disrupt the attack chain.
Not every person in an organization is made equally. Different people have different risk profiles, which means you need different protection techniques. Kristin explains that segmenting your user base (IT people, “VIP” users, general population, etc), and applying different security profiles may be a good approach. She explains that this concept has been implemented at IBM and people were given disposable hardened Linux images to minimize the impact of incidents.
Typically, an attack has 5 stages. In other words, you can try to implement mechanisms to disrupt an attacker in each of those 5 stages: Break-in, Latch-on, Expand, Gather, Exfiltrate.
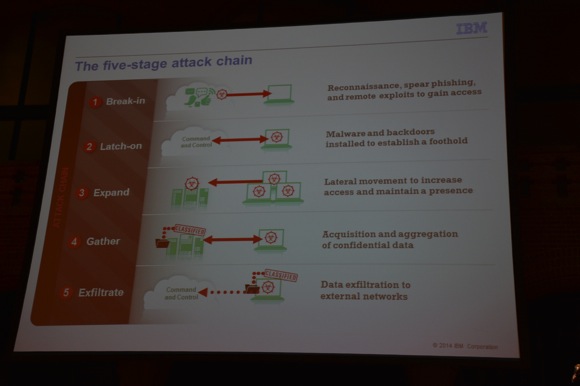
Lesson 5: It also means knowing how to communicate effectively with senior executives.
Use small words. Don’t make things complicated. Don’t use big ISO standards, but use analogies management understands. For example: “Implementing security is like building a house”. Some things are mandatory ( = basic security), some things “should” be done and others can be done to be better than the rest. If you’re serious about security, and want to improve security at your company, you should
- Train people
- Have a CCERT
- Have a collaborate workplace environment
- Build security inside, implement in the day-to-day work
- Manage IT security hieg
- Manage 3rd party compliance
- Manage the digital identity lifecycle
- Assure data security
- etc
FInally, use little words, accept that there is no perfection and be humble.

Slides: http://haxpo.nl/hitb2014ams-kristin-lovejoy/
About Kristin Lovejoy
Kristin Lovejoy is the General Manager of the IBM Security Services Division, charged with development and delivery of managed and professional security services to IBM clients world-wide. Prior to her role in Services, Kris was IBM’s VP of Information Technology Risk and Global CISO, responsible for managing, monitoring and testing IBM’s corporate security and resiliency functions globally, where she also acted as Chairman of IBM’s IT Risk Steering Committee, co-Chair of IBM’s Data Security Steering committee, co-Chair of the IBM’s Social Networking committee, and member of IBM’s Enterprise Risk Steering Committee. Today Kris is a member of a number of external boards and advisory panels, including SC Magazine’s Editorial Board, Forrester’s Security and Risk Council, and Grotech Ventures. Before joining IBM, she was the CTO, CIO and VP of Support and Services at Consul which was acquired by IBM in 2007 as well as VP of Security Assurance Services for TruSecure Corporation.
Kris is a recognized expert in the field on security, risk, compliance and governance, with appearances on CNBC, NPR and WTOP. Within the past five years she has been recognized as 2012 Compass Award Winner by CSO Magazine, one of E-Week’s 2012 “Top Women Women in Information Security That Everyone Should Know”, Top 25 CTO by InfoWorld, as Top 25 Most Influential Security Executives by Security Magazine. Ms. Lovejoy holds U.S. and EU patents for Object Oriented Risk Management Models and Methods.
© 2014 – 2021, Peter Van Eeckhoutte (corelanc0d3r). All rights reserved.


