12,949 views
 Metasploit module : HTTP Form field fuzzer
Metasploit module : HTTP Form field fuzzer
Introduction
About a month after releasing an ftp client fuzzer module for Metasploit, I decided to release yet another fuzzer module I have been working on over the last few weeks.
This new module can be used to audit web servers/web server plugins/components/filters, by fuzzing form fields and optionally fuzz some header fields.
While this type of fuzzing/audits most likely won’t reveal bugs in the most common webserver platforms themselves (Apache, IIS, etc), I am convinced that there are a lot of other web server components out there that may not properly validate input from form fields or header fields.
A few hints :
- custom modules / isapi components / custom dll’s that process input
- admin consoles
- embedded webservers
- etc
The module
This new fuzzer module was added to the Metasploit framework earlier today (svn release r11013 and up), and can be found in /modules/auxiliary/fuzzers/http. The module file is called http_form_field.rb
If you are using a svn based copy of the framework, you can get the module very easily (and all future updates) by updating your svn copy. More info about creating a svn copy and about updating the svn can be found in the post about the client ftp fuzzer module.
Anyways, this is what the module will do :
- It will connect to a webpage (referred to by the "URL" option), parse the body and identify all forms & form fields contained within those forms.
- Then, it will create POST (or GET, depending on the form method) requests, sending those fields back to the webpage provided in the "action" field of the form, and fuzz the contents of the fields while doing that. It will only fuzz one field at a time.
- By default, only text fields, password fields, and inputtextbox fields will be fuzzed, but you can define other field types by setting the "TYPES" parameter.
- In additition to that, it can optionally fuzz header fields as well. It will use the existing headers (and add some common headers if they are missing) and fuzz each one of those headers using POST/GET requests.
Using the module
Loading the module is as easy as doing this :
root@bt:/pentest/exploits/trunk# ./msfconsole -n
msf > use auxiliary/fuzzers/http/http_form_field
msf auxiliary(http_form_field) >
The available module options are :
msf auxiliary(http_form_field) > show options Module options: Name Current Setting Required Description ---- --------------- -------- ----------- ACTION no Form action full URI. Leave empty to autodetect CODE 200,301,302 yes Response code(s) indicating OK CYCLIC true yes Use Cyclic pattern instead of A's (fuzzing payload). DELAY 0 yes Number of seconds to wait between 2 actions ENDSIZE 200000 yes Max Fuzzing string size. FIELDS no Name of the fields to fuzz. Leave empty to fuzz all fields FORM no The name of the form to use. Leave empty to fuzz all forms FUZZHEADERS true yes Fuzz headers Proxies no Use a proxy chain RHOST yes The target address RPORT 80 yes The target port STARTSIZE 1000 yes Fuzzing string startsize. STEPSIZE 1000 yes Increment fuzzing string each attempt. STOPAFTER 2 no Stop after x number of consecutive errors TIMEOUT 15 yes Number of seconds to wait for response on GET or POST TYPES text,password,inputtextbox yes Field types to fuzz URL / no The URL that contains the form VHOST no HTTP server virtual host
- Action : By default, this field will be auto-populated. It is used to store the "action" variable of each form. In essence, this is the target URL that is used when submitting form contents to the webserver. So, if you leave this field empty, the fuzzer will attempt to detect the form action and use it as a target for the fuzzing operations. If you need to specify an action URL yourself (because the autodetection routine is not accurate enough), then it will be used for all forms on the page. This means that you should use this in conjunction with the FORM parameter (so you would be fuzzing the correct form fields against the correct action page).
- Code : This parameter contains a comma separated list of response codes that are considered to be OK
- Cyclic : When set to true, the fuzzdata will consist of a cyclic pattern. If you set this value to false, the fuzz data will be made up of a long string of A’s
- Delay : This parameter allows you to specify the number of seconds to wait between two fuzz operations.
- Endsize : This is the maximum size of fuzzdata that will be sent to the target. When the maximum length has been reached, the fuzz operation will end.
- Fields : If you leave this option empty, then all fields in the form (limited to field types specified in the TYPES option) will be subject to fuzzing. If you want to limit the fuzz to certain fields only, then you populate the option with a comma separated list of field names.
- Form : When empty, the fuzzer will attemt to identify and enumerate all forms on the page, and fuzz all of the fields in all of those forms. If you only want to fuzz specific form(s), you can put a comma separated list of form names/ids in this field.
- Fuzzheaders : If this option is enabled, then the fuzzer will also fuzz http request header fields after fuzzing form fields.
- Proxies : You can use this field to specify a proxy chain
- Rhost : This option is used to specify the target host
- Rport : This option is used to specify the target port
- Startsize : This parameter allows you to specify the start length of the fuzz data
- Stepsize : This parameter defines the number of chars to increase the fuzz data with after each fuzz
- Stopafter : This parameter defines the number of error conditions to occur before giving up
- Timeout : Use this option to specify the number of seconds for each get/post request to wait for a response
- Types : This option can be used to define the type of form fields to fuzz. When left empty, it will fuzz all fields.
- URL : This option defines the exact url of the page that contains the form to fuzz.
- Vhost : Use this option if you want to use a host header name.
Important note : if you want to clear a certain option, don’t set it to an empty string (set
The advanced options are :
msf auxiliary(http_form_field) > show advanced Module advanced options: Name : BasicAuthPass Current Setting: Description : The HTTP password to specify for basic authentication Name : BasicAuthUser Current Setting: Description : The HTTP username to specify for basic authentication Name : FingerprintCheck Current Setting: true Description : Conduct a pre-exploit fingerprint verification Name : SSL Current Setting: false Description : Negotiate SSL for outgoing connections Name : SSLVersion Current Setting: SSL3 Description : Specify the version of SSL that should be used (accepted: SSL2, SSL3, TLS1) Name : UserAgent Current Setting: Description : The User-Agent header to use for all requests Name : WORKSPACE Current Setting: Description : Specify the workspace for this module
- BasicAuthPass and BasicAuthUser can be used if the target website requires authentication prior to accessing it (Basic authentication only)
- FingerPrintCheck has no use in this fuzzer
- You can set SSL (and SSLVersion) if the target website requires https. Don’t forget to change the rport option accordingly
- Useragent allows you to define an alternative User Agent field. The default value (hardcoded into the fuzzer) is "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.9.0.15) Gecko/2009102814 Ubuntu/8.10 (intrepid) Firefox/3.0.15"
Example :
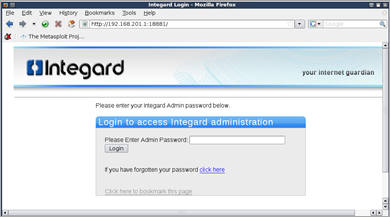
Let’s use the module to test the Integard admin login page (and reproduce the vulnerability that was reported here). I installed a vulnerable copy of Integard Home on a test computer (192.168.201.1). From my attacker machine, I can access the login page on port 18881 :
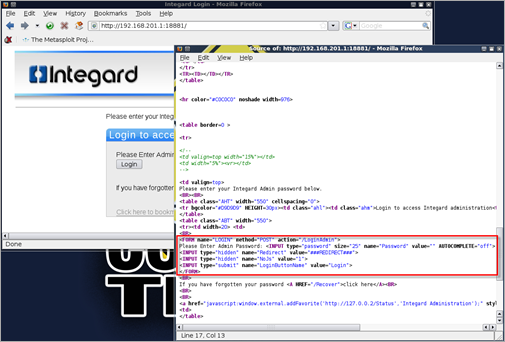
The source of the page reveals the following form :
- The form fields will be posted to /LoginAdmin
- There are 3 fields (password, Redirect, NoJs) and a submit button. We’ll fuzz the password field in this example.
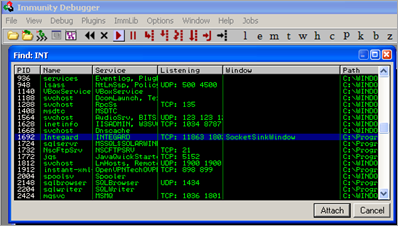
Next, I attached Immunity Debugger to Integard.exe and let the application run inside the debugger.
Configuring the Metasploit form field fuzzer for this case is really easy. We only have one form, so we can try to let the plugin auto-configure itself. The only 3 parameters we’ll need to specify are :
- rhost / vhost
- rport
- URL
msf auxiliary(http_form_field) > set rhost 192.168.201.1 rhost => 192.168.201.1 smsf auxiliary(http_form_field) > set vhost 192.168.201.1 vhost => 192.168.201.1 smsf auxiliary(http_form_field) > set rport 18881 rport => 18881
The URL option already contains "/", so that will work fine in this case. The default field types are "text", "password" and "inputtextbox", so that means that the fuzzer will only look at the password field.
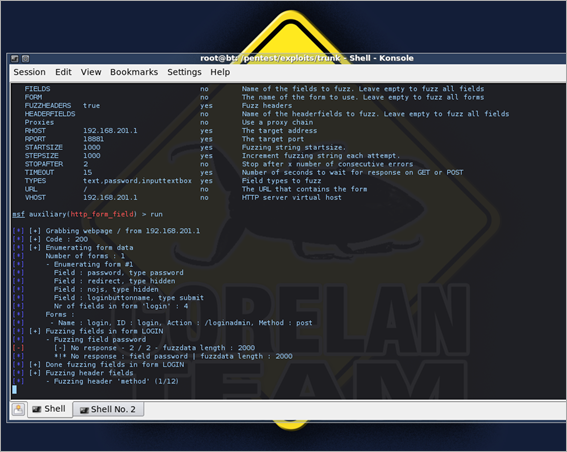
Now simply issue "run" and the fuzzer will start fuzzing :
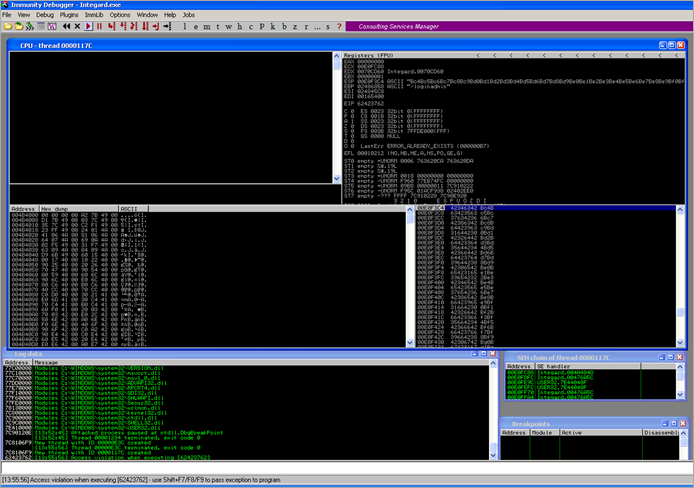
You will notice that the fuzzer will report a "No response" when fuzzing the password field with 2000 bytes. Look at the debugger :
Nice : we control EIP and can see the payload on the stack. Game over :)
Finally :
If you have questions / comments / feedback about the module, feel free to leave your comments below, or drop by in the corelan IRC channel on freenode.
Have fun !
 Copyright secured by Digiprove © 2010 Peter Van Eeckhoutte
Copyright secured by Digiprove © 2010 Peter Van Eeckhoutte
© 2010 – 2021, Peter Van Eeckhoutte (corelanc0d3r). All rights reserved.
Similar/Related posts:
Comments are closed.
Corelan Training
Check out our schedules page here and sign up for one of our classes now!
Donate

Your donation will help funding server hosting.
Corelan Team Merchandise
Corelan on Slack
You can chat with us and our friends on our Slack workspace: