28,300 views
 Pastenum – Pastebin/pastie enumeration tool
Pastenum – Pastebin/pastie enumeration tool
Introduction
When conducting a pen-test, the process typically starts with the reconnaissance phase, the process of gathering information about your target(s) system, organization or person.
Today, we want to present a tool that can be added to your reconnaissance toolkit.
Text dump sites such as pastebin and pastie.org allow users to dump large amounts of text for sharing and storage.
As these sites become more popular the amount of sensitive information being posted will inevitably increase.
Pastenum is designed to help you find that information and bring it into one easy to read location.
The hope is it will allow internal security teams to run simple queries about their companies and determine if they have sensitive information residing in one of these text dumps. It will also help pen-testers with the recon phase by allowing them to enumerate more data faster.
In order to do so, it uses a series of search queries for keywords, provided by the pentester. Since it queries public sources (and not the target network itself), this should be stealth to the target.
Installing the tool
To use Pastenum you will need ruby 1.9.2.
I recommend using Ruby Version Manager (RVM) on linux found at http://rvm.beginrescueend.com/. Once that is installed you need several gems, they are listed in the README file included with pastenum.
What follows below is a quick procedure outlining the exact steps on how to get everything installed on Ubuntu. Steps should be similar on other OSs.
As stated on the rvm website, it’s important to run the installation commands with a non-root user account. If you want to install rvm system-wide as root, please check the rvm website for the exact installation steps.
Every time root permissions are required in the procedure below, sudo will be used. (So make sure the user account you are using has sudo permissions).
On certain security distributions (BackTrack for example), the only available user account is root. Since it is not recommended to use root for the procedure below, you will have to create a non-root useraccount first and use that account to perform the installation.
Example :
root@bt:~# useradd -d /home/corelanc0d3r -m -s /bin/bash corelanc0d3r root@bt:~# passwd corelanc0d3r Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully
Now become that user account, using the profile of the user :
root@bt:~# su corelanc0d3r corelanc0d3r@bt:/root$ echo $HOME /home/corelanc0d3r
Make sure the user has sudo permissions. Run ‘visudo’ (as root) and add a line
corelanc0d3r ALL=(ALL) ALL
That’s it.
Prerequisites
# cd ~
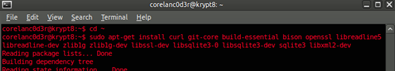
# sudo apt-get install curl git-core build-essential bison openssl \
libreadline5 libreadline-dev zlib1g zlib1g-dev libssl-dev \
libsqlite3-0 libsqlite3-dev sqlite3 libxml2-dev libxslt1-dev
(answer "Y" when asked to install packages)
Install rvm
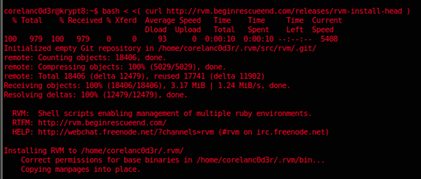
bash < <( curl -s https://rvm.beginrescueend.com/install/rvm )
Edit bashrc
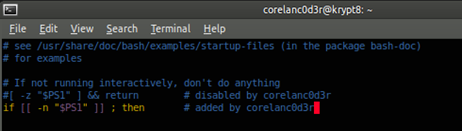
vi ~/.bashrc
1. Look for line
[ -z “$PS1” ] && return
and replace it with
if [[ -n "$PS1" ]] ; then
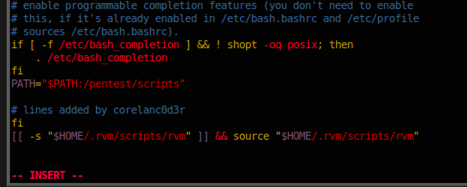
2. At end of file, add
fi [[ -s "$HOME/.rvm/scripts/rvm" ]] && source "$HOME/.rvm/scripts/rvm"
Save the file
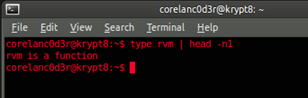
Close the console and open a new console. Verify that rvm is working :
type rvm | head -n1
(this should return "rvm is a function")
Install ruby
To install ruby v1.9.2 (which is what we need), run
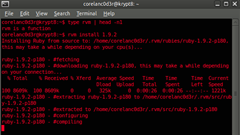
rvm install 1.9.2
Note : If you want to install other ruby versions as well, simply run a similar command for each version you want to install:
rvm install 1.8.7 rvm install 1.9.1
That’s it
Set ruby version
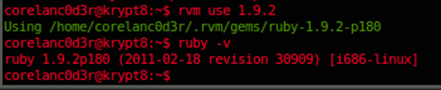
Any time you want to run a ruby application that requires a specific ruby version, you can ‘activate’ that specific version. In our case, we need ruby v1.9.2 :
rvm use 1.9.2
If you want to set this version as the default ruby version, issue the following command :
rvm --default use 1.9.2
Verify that this version is now active :
ruby -v
Install gems
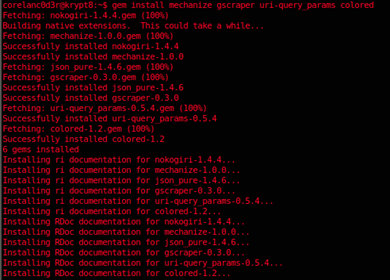
As stated earlier, we need to install a couple of gems to satisfy the script dependencies :
gem install mechanize gscraper uri-query_params colored
Download pastenum
We’re all set.
Head over to http://redmine.corelan.be:8800/projects/corelan-pastenum, go to "Files" and download the latest version of the script.
Extrac the file
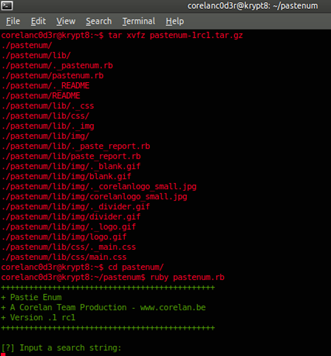
tar xvfz pastenum-1rc1.tar.gz
You should see a folder called "pastenum".
Okay, ready to rock ‘n roll !
Usage & Examples
Once you have all of the prerequisites installed the application is very easy to use.
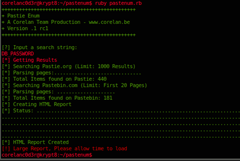
As shown in the picture above, just run "ruby pastenum.rb" and enter your search at the prompt.
When the tool has completed the search, you can view the report in the source directory.
A word of warning, if you get more then 100 results back it can take some time to render the page, please be patient.
Some examples :
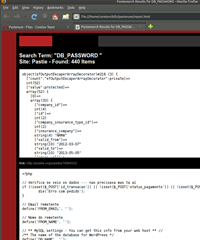
- DB_USER DB_PASSWORD (WordPress configs)
- priv8 ("Hacker" tools and other "Malicious" content)
- phpMyAdmin SQL Dump (phpMyAdmin dumps )
- sa sasa (List of potentially compromised hosts)
- 123456 qwerty (Password list, Bruteforce tools and hacked accounts)
(Be creative)
To view the report, open report.html in a browser (and wait)
firefox report.html
That’s it – hope you like it !
Questions
If you have got questions, bugs or features request, please feel free to email: nullthreat(at)corelan.be or join the team in IRC: irc.freenode.net #corelan
Alternatives : Pastebin-scraper
Shortly after pastenum was released by nullthreat, Andrew MacPherson decided to take things one step further and published an online tool that will "scrape" various resources (similar to what pastenum does). You can download the php code or run online queries here : http://andrewmohawk.com/2011/03/25/pastebin-scraper/
More info about his scraper can be found here
Good job Andrew !
© 2011 – 2021, Elliott Cutright. All rights reserved.


Pingback: rfdslabs » Post Topic » Information Disclosure with Pastebin.com
Pingback: Pastenum – Devenez un curacker efficace !
Pingback: Liens du jour 24 March 2011 | LouWii's Blog
Pingback: AndrewNohawk » Blog Archive » Pastebin Scraper
Pingback: Week 12 In Review – 2011 | Infosec Events
Pingback: Week 12 In Review – 2011 | Portable Digital Video Recorder
Pingback: pastenum – Another nice recon tool | Portable Digital Video Recorder