1,494 views
 Setting up InfoExpress CyberArmor Suite 3.5
Setting up InfoExpress CyberArmor Suite 3.5
CyberArmor is a really excellent personal firewall. The CyberArmor suite consists of a Policy Server (and Policy Manager) used to create policies, a CyberServer (used to capture logs and alarms, optional), a Secure Ping Server (optional) and an MSDE back-end. More information can be found at http://www.infoexpress.com/security_products/firewall_overview.php
The product runs on Windows platforms and allows for centralized management (including updating rulesets) of personal firewalls. The nice thing about CyberArmor is that it allows a lot of flexibility in terms of determining where a computer is located, and the ability to apply different rulesets based on the location. This location awareness is the core foundation of the tool, and goes much further than the location awareness found in products such as Symantec or Microsoft. Futhermore, the tool does not only block or allow traffic based on rules, but it also contains application filtering, and intrusion prevention.
You’ll need a Windows server (2003 R2 in my case), with IIS installed. You’ll need a web server certificate (but you can generate a certificate with SelfSSL from the IIS resource kit if you don’t have access to a CA).
Before you begin, make sure NOT to put the server in a domain. CyberArmor suite 3.5 doesn’t support servers that are member of a domain, so make sure not to put in in a domain. Ever.
Second, make sure to turn off DEP. Edit the boot.ini of the server and change /noexecute=optin to /noexecute=AlwaysOff
Reboot before you start installing.
In my environment, the installation of CyberArmor Suite 3.5 failed on Windows 2003 R2, so I had to install 3.2 and then upgraded to 3.5, which did the trick just fine.
The installation for both 3.2 and 3.5 goes as follows :
- Make sure all windows patches and updates have been applied on the server.
- Make sure there is only one website (default), and that it’s reachable over http and https
- Create a ini file called casuite.ini and put it in the same folder as where casuite.exe (which is the installer) resides
- Open the ini file and put the following line in the file : Logging=True
- Start the installation using the following command : casuite.exe /M=casuite.ini
- Click "Accept" at the "Software License Agreement Screen"
- Click "Next" at the "CyberArmor 3.5 Suite Installation Welcome" Screen
- Click "Next" at the the "CyberArmor 3.5 Suite Installation" screen (With release notes).
- Select all the server related options, and click "Next". Initially it is recommended that you install all components on the same system.
- Leave the Destination Directory as the default, or change it if desired, and Click "Next" at the "Select Destination Directory" Screen
- Click "Next" at the "Select Program Manager Group" Screen.
- Click "Next" at the "Policy Server Requirement" screen.
- Enter and confirm the password for the root account, that’s the account that you use to log in to policy manager.
- Select "Logging with FRAMD database" (Default) and click "Next" at the "Select CyberServer Option" screen.
- Leave the log directory as default (c:\csdata) or change of desired and click "Next" at the "Select CyberServer Log Destination Directory" screen.
- Click "Next" at the "CyberServer Bridge Requirements" screen.
- Leave the SQL Server directory as default (C:\Program Files\Microsoft SQL Server\) or change if desired and click "Next" at the "Select Microsoft SQL Server Destination Directory" Screen.
- Leave the Database directory as default (C:\Program Files\Microsoft SQL Server\) or change if desired and click "Next" at the "Select Database Destination Directory" screen.
- Enter and confirm the password for the ‘sa’ account, which is the administrator password for the SQL server and click "Next" at the "Select Microsoft SQL Server Administrator Password" screen.
- Click "Next" at the "Ready to Install" screen.
- The installation will start, Setting up Microsoft SQL Server Desktop Engine screen will appear (this could take up to 20 minutes). Other shell screens will pop up as well.
- A screen will pop up to configure the CyberArmor Policy Manager. Enter the real IP address or FQDN name for the server (do not Enter the WINS Server name) as a Policy Server Name. Click "OK".
- Click "OK" at the "Configure PolicyServer" screen (This may take a minute)
- At the "CyberArmor Policy Manager" screen, make sure the Server name is the same IP address or server name entered in step 22. The proxy port should be left as default (11175). The username should be ‘sa’ and the password (hidden) is the same password that was entered for the ‘sa’ account in step 19. Leave the Audit Section the same (Number of days to keep the Audit records is 180). Do not import CyberArmor Binary at this step. Click "OK".
- The next screen is "Configure CyberServer" screen, click "OK".
- Leave all the defaults the same at the "CyberServer Setup" screen, Make sure Log using FRAMD is checked, and the number of days to keep the logs is 90 (these settings can be changed later once the installation is complete) Everything else on this screen should be unchecked, or is grayed out.
- Click on the Connection tab of the "CyberServer Setup" screen. Again leave all the defaults. Listening Port should be 11162, Encryption Key should be Log11160, and Max Notification Size should be 750000. The next 2 check boxes (Clients must provide password if encryption is disabled, and Log events to the debug log file) should be unchecked.
- Click on the Connection tab of the "CyberServer Setup" screen. This tab is used for configuring a Regional Server in a distributed environment. Again leave all the defaults. Regions Reposnsible and Policy Server Address should be blank, Port betweeb CS and PS should be set to 11163, and Replication interval should be set to 180 seconds. Click "OK".
- At the next screen, Leave the port number for the "Secure ping server" as the default (should be 11179) and click "OK".
- At this point the CyberArmor Suite Installation has been completed. Click Finish to exit the installation
- The system has to be rebooted for the installation to complete, and services to be started. Click "OK" to restart the computer.
- Once the computer has been restarted, Launch Policy Manager (Start \ Programs \ InfoExpress \ CyberArmor Policy Manager \ Policy Manager)
- The Logon to the Policy Server screen will appear. Server name should be the real IP address or DNS name of the serverentered in step 22. User Name should be ‘root’ and Password should be the password that was specified in Step 13. Click OK
- Enter the Registration ID and the Registration Code and click OK. Make sure that that "End Systems" screen is populated with data (Types of end systems should show CorpDesktop, CorpLaptop, and EmployeeOwned).
-
CyberArmor suite now is completely installed and is ready to use.
Now do the same for CyberArmor Suite v3.5
Once you have v3.5 installed, log on to the policy manager. You’ll see the 3 default End User Systems. If you are installing a new system, the first thing you should do now is create a Region and bind a End User System to a region (or create a new end user system and bind it to a region). You’ll have to "check out" before you can modify settings. Don’t forget to check in again when you have finished editing.
When you have created the policies and tested the policy, you can deploy a new policy. This will create a folder under c:\inetpub\wwwroot\cyberarmor containing the current date/time of deployment, the region, the end user system, and then the installation packages. You can install new clients using pcainst.exe (Win2K/XP) or pcamsiinst.exe (Vista) from this folder. Once the clients have been installed (and when you’ve configured automatic updates), your clients will automatically pull down updates when new versions have been deployed.
That’s it – in a nutshell.
When you are installing a new CyberArmor server and you want to import the settings from another machine (because of a migration, or disaster recovery), this is what you should do
- Make sure v3.5 works, with default settings
- Get the pcarm.ini and pcarm.pro file from one of the policies under c:\inetpub\wwwroot\cyberarmor) Note that each end user system has their own pcarm.ini and pcarm.pro file
- Log on to policy manager
- Go to "Tools" – "Import Shared Settings"
- Select the pcarm.ini file and wait until the import has completed
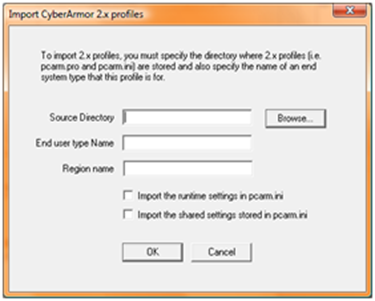
- Go to "Tools" – "Import 2.x profile"
- Select the pcarm.pro file, enter the name of the End User type, and the name of the Region Name. Make sure to ENABLE "Import the runtime settings in pcarm.ini" and DISABLE "Import the shared settings stored in pcarm.ini". Do this for for each end user system type.
When the import has completed, you should now see the Region and End User system that was created on the old machine.
Next, "check out" and go to "Rules" – "Others"
Edit the "group" variable, remove the hash, and replace the hash with
Check in again, save the changes, and you are now ready to deploy again.
Note on deploying : You’ll see various "Engine" versions in the deploy window. This is what these versions mean :
Pre 3.5 Clients :
– R = Regular Engine (will require reboot before upgrade takes place)
– NB = No Boot Version
– NC = No Encryption Version
– B = Big Version support
– S = SSL Version
3.5 and later clients :
– ST = Standard Client, does not require user intervention
– V = Verbose Client, requires user interaction.
In my opinion, the ST version is the way to go.
If you have questions on how to create policies or set up the location awareness, drop me an email at peter.ve@telenet.be
© 2008 – 2021, Peter Van Eeckhoutte (corelanc0d3r). All rights reserved.