21,098 views
 Securing Windows Server 2008 and Active Directory
Securing Windows Server 2008 and Active Directory
According to Microsoft, Windows Server 2008 is the most secure Windows server version ever.
Windows 2008 does include many features that will help increase overall security of the OS, or assist you with securing AD, the network, etc. Most of the features/roles available in Windows 2008 are not being installed in a default installation of Windows 2008, leaving the OS in a more or less ‘secure’ state right after installation. The attack surface of a default Windows 2008 server may be smaller than it was under NT4, 2000 and 2003, but concluding that Windows Server 2008 is secure, may be one bridge too far.
Microsoft has published a paper on the differences between 2003 and 2008, which includes some security related information. The document can be downloaded from “Changes in Functionality from Windows Server 2003 with SP1 to Windows Server 2008”
I’ll use this post to explain some of the recommended hardening techniques, and list some additional tweaks/settings that can (and imho should) be applied to a Windows 2008 server in an attempt to further harden the OS.
This document consists of the following parts
For Windows 2008/AD servers :
– Using GPOAccelerator to create GPO’s that can be applied to AD and to regular servers
– Provide some recommended settings that should be configured to a Domain GPO, including Domain Password Policies and Fine Grained Password Policies
– Provide some recommended settings that should be configured to the Domain Controller’s GPO,
– Provide some recommended settings that should be configured to regular server GPO’s
– Using GPOAccelerator SCE Extensions to further secure AD and servers using GPO’s
– Create your own extensions and create custom Security Templates
– Use the custom Templates to actually set out the various GPO’s (based on the recommendations that are given in this document). You don’t want to go in and change all the GPO’s manually. It is better to create your own templates and then apply these templates to the corresponding GPO’s.
– Using Security Configuration Wizard to secure servers that have a specific role
For standalone/”high security” servers :
– Using GPOAccelerator and Security Templates to secure “standalone” servers
For all servers
– Additional (Custom) settings that should be applied to any server, and general security recommendations to secure AD
Download section : I have made my customized Security Templates for AD Domains, for AD DC’s, for member servers and for high security hosts available for download. You can find the link at the bottom of this post.
Note : this document is not the ultimate complete security guide for 2008. It just provides some tips & tricks to increase the overall security level.
General
Before going into the various procedures of securing AD and servers, I’ll briefly discuss some of Microsoft’s
recommendations on tackling the attack surface that is still present in Windows 2008. The Windows Server 2008 Security Guide document (content also available on Technet at http://technet.microsoft.com/en-us/library/cc264463.aspx) makes a clear distinction between (EC) Enterprise Security (I’ll interpret this as being servers that need to be part of the Enterprise, the Domain, or have roles/features that require integration and/or interaction with AD DS and/or other services within the Enterprise… for whatever reason) and servers that requires specialized security (SSLF). I’ll interpret the latter as servers that don’t need to be part of the domain, or that can have an elevated security level applied. Some of the settings in this blog post will apply to both environments, others will only apply to the servers with a higher security level requirement. If a setting only needs to be applied to these servers, I’ll mention this (so you don’t break stuff. After all, the SSLF model focusses primarily on security, and this will result in limited functionality)
In both scenario’s, a Tool / Windows Shell script called GPOAccelerator can be used to set up a security baseline, either using EC Settings, or SSLF Settings (SSLF is not a supplement on top of EC, it’s just a different set of rules). GPOAccelerator can be downloaded from http://www.microsoft.com/downloads/info.aspx?na=47&p=2&SrcDisplayLang=en&SrcCategoryId=&SrcFamilyId=12ac9780-17b5-480c-aef7-5c0bde9060b0&u=details.aspx%3ffamilyid%3dA46F1DBE-760C-4807-A82F-4F02AE3C97B0%26displaylang%3den
First things first
Right after installing the Windows 2008 OS, you should consider running the following steps :
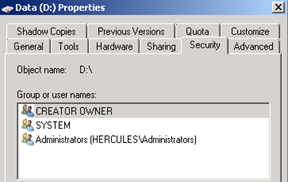
– Secure the filesystems. Change the NTFS Security on all non-System partitions to :
(Basically, remove “Everyone” and “SERVER\Users”)
– Change NTFS Security on the following executables, and change the ACL to BUILTIN\Administrators and System (Full Control) only :
arp.exe
at.exe
cacls.exe
cmd.exe
rexec.com
command.com
debug.exe
edit.com
edlin.exe
finger.exe
ftp.exe
tracert.exe
ipconfig.exe
nbtstat.exe
net.exe
netsh.exe
cscript.exe
wscript.exe
nslookup.exe
netstat.exe
regedit.exe
regedt32.exe
route.exe
rsh.exe
runonce.exe
syskey.exe
telnet.exe
rcp.exe
xcopy.exe
Note : some of these files may be missing on a Windows 2008 machine, other Windows 2008 files may be missing from this list, but I’m still reviewing the list of files… In the meantime, you can use the same list for hardening a Windows 2000/2003 server as well.
– Do NOT run services as NetworkService or LocalService, but use regular accounts instead. On IIS7 servers, do not run ASP.NET in Full trust or don’t run websites with NetworkService or LocalService accounts
This setting will prevent Token Kidnapping (http://www.argeniss.com/research/TokenKidnapping.pdf)
For Active Directory, take the following steps as well (in fact, you need to think about these things when you design your AD)
– Keep your DC’s dedicated to the DC role.
– Delegate access, don’t use the admin accounts. Create the toplevel OU structure, create admin user accounts and a Admin Group. Change the security on this group so only a limited set of admins can change membership of this admin group. Delegate Full Control to the toplevel OU structure, but NOT to the domain. This will help you ensuring the integrity, availability and security of your AD.
Don’t forget to set strong passwords to your admin accounts.
– DON’T use the Domain Admins group. Don’t make anyone member of this group, and keep the password secret. There’s nothing really that cannot be delegated. For more information about delegating access to your custom admin groups in order to be able to perform certain admin tasks, see near the bottom of this post.
– Rename the administrator account, create a fake “administrator”. Don’t forget to copy the contents of the personal/account information fields, so the fake administrator really looks like the administrator :) Of course, keep this fake administrator disabled.
GPOAccelerator – Creating a baseline
GPOAccelerator will allow you to create, test and deploy security settings. The tool creates OU’s / GPO’s, so you can link them in your production AD environment, or you can use the .inf files that come with GPOAccelerator to apply settings to standalone servers. It is advised to test GPOAccelerator before using it in production AD.
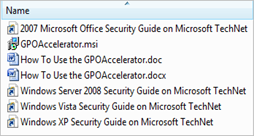
When you unzip GPOAccelerator, you will find these files :
Start by installing GPOAccelerator.msi
Roughly, this is what gets installed :
| C:\Program Files\GPOAccelerator>dir Volume in drive C has no label. Volume Serial Number is ACFE-FB99 Directory of C:\Program Files\GPOAccelerator 17/04/2008 23:52 C:\Program Files\GPOAccelerator>dir GPMCFiles Directory of C:\Program Files\GPOAccelerator\GPMCFiles 17/04/2008 23:52 C:\Program Files\GPOAccelerator>dir “SCE Update” Directory of C:\Program Files\GPOAccelerator\SCE Update 17/04/2008 23:52 C:\Program Files\GPOAccelerator>dir “Security Templates” Directory of C:\Program Files\GPOAccelerator\Security Templates 17/04/2008 23:52 C:\Program Files\GPOAccelerator> |
As you can see, a Windows Shell Script file (Command Line, gpoaccelerator.wsf) and an executable (GUI, gpoaccelerator.exe) were placed in the installation folder, along with some other files and folders.
For example, the folder “GPMC files” contains 4 folders.
OSG = Office Security Guide
VSG = Vista Security Guide
WSSG = Windows Server Security Guide
XPG = XP Security Guide
The WSSG folder contains the following files and folders :
| Directory of C:\Program Files\GPOAccelerator\GPMCFiles\WSSG
17/04/2008 23:52 |
These files will be used by the GPOAccelerator tool to create GPO objects, in this case for Windows Servers.
If you are only interested in creating the GPO’s with the EC settings, run GPOAccelerator.wsf /WSSG /Enterprise
If you want to create special OU’s, then use the /LAB option (so GPO’s are linked to these OU’s, and not to OU’s in your production environment)
(Review the “How To Use the GPOAccelerator.doc” document for more command-line options.)
We’ll come back to the command line features, let’s have a look at the GUI component first, which is in fact nothing more than a wizard that will create the exact syntax/parameters to run the Script.
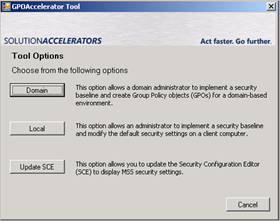
Log on as Domain Admin and launch the GUI by running GPOAccelerator.exe
You can either create GPO objects in the domain, or create a Security Policy that can be applied to standalone systems. Finally, the GUI allows you to update the SCE to display MSS security settings. You’ll need this last option (so you need to run this at least once) in order to be able to display/edit the settings that were written by the “Microsoft Solutions for Security” group. Don’t run this yet, I’ll show you how this works later on.
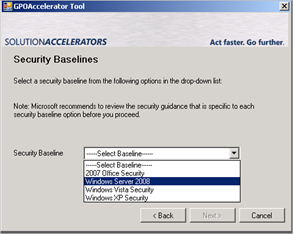
Click “Domain” and select the desired Security Baseline from the dropdown list. In our example, this is Windows Server 2008
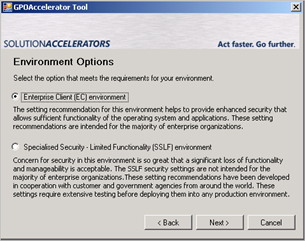
Select either the Enterprise Client (EC) or SSLF environment.
We’ll start with the EC first
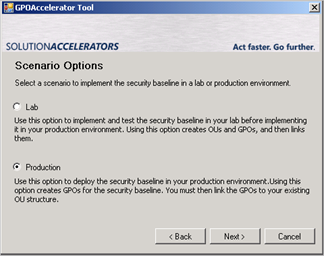
The next page will ask you whether you want to implement the baseline in lab or production environment. Normally, if you have a clean LAB environment, you could choose LAB, but since I don’t want the tool to start messing up my own OU structure, I just want the GPOs to be created, and I’ll link them to whatever OU I want later on. So I’ll choose Production for now
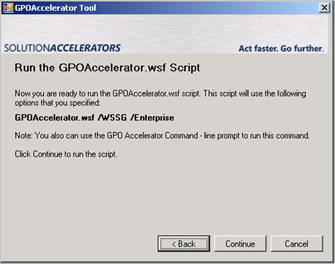
The last page shows the command that will be run as a result of our selections. As stated before, this tool is nothing more than a GUI wizard on top of the script.
So basically, if you would run “GPOAccelerator.wsf /WSSG /Enterprise” from command line, then you would get the same results.
Just keep in mind, if you want to use the command line in production environment :
– Log on with Domain Admin rights
– Launch “Command-line here.cmd” with administrator privileges (Run as administrator)
– type cscript GPOAccelerator.wsf /WSSG /Enterprise
Anyways, we’ll let the GUI run the scripts for now – the result should be exactly the same.
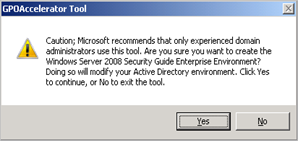
If you press “Continue”, you’ll get the following warning
Click “YES” to continue (at your own risk, of course :-) )
Click OK when asked
Wait until the process has completed
and accept the fact that you will have to link the GPOs to the appropriate OUs yourself.
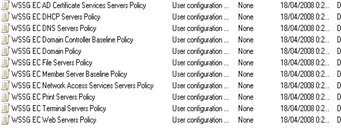
Open Group Policy Management console and verify that the objects have been created
You can use these GPOs in conjunction with the corresponding roles and features to secure these installed roles/features.
Let’s have a look at some common GPO’s and what we can do to further secure these GPO’s before you apply them
Modifying the WSSG EC Domain Policy
While this GPO does not really apply directly to one particular server, it is still good practise to set/review these settings as your overall security plan for your servers.
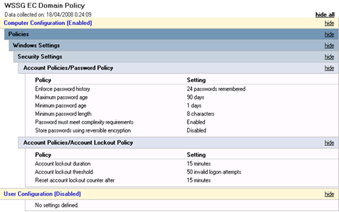
Default Domain Password Policy
The Domain (Password) Policy that is created by GPOAccelerator states
Password history : 24 passwords
Max password age : 90 days
Min password age : 1 days
Min password length : 8 characters
Password complexity : enabled
Store passwords using reversible encryption : disabled
Account lockout : 15 minutes
Account lockout threshold : 50 invalid attempts
Reset lockout counter after : 15 minutes
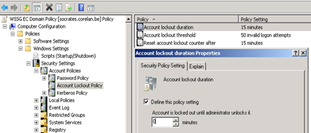
I would strongly recommend
– change the Account lockout during to forever (until admin unlocks) : change value to 0
– change the lockout threshold to 3 or 5 attempts
– change the lockout counter to 30 minutes or more
Additionally, I would recommend configuring the following settings for the Domain Policy :
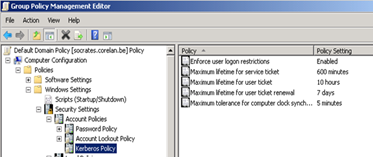
Computer Configuration – Policies – Windows Settings – Security Settings – Account Policies – Kerberos Policy
Enforce user logon restrictions : Enabled
Max lifetime for service ticket : 600 minutes
Max lifetime for user ticket : 10 hours
Max lifetime for user ticket renewal : 7 days
Max tolerance for computer clock synchronization : 5 minutes
Note : Depending on how you want to keep the client’s clock up to date, you may have to allow your users to change the system time (For example : if you are running some command to sync the clock from a loginscript, then the user account needs to have permissions to change the system time). You can define this setting under “Local Policies – User Rights Assignments”. If you are using NTP, then this setting is irrelevant and can be limited to your IT Admin group
Fine Grained Password Policies
Windows 2008 introduces the concept of Fine Grained Password Policies. This feature allows you to specify multiple password policies in a domain, by basically linking a password policy to a set of users (inetOrg Person objects, or Global Groups). Unfortunately you cannot assign a Fine Grained Password Policy to members of a OU.
In order to be able to define a Policy, the domain needs to be in 2008 functional mode. By default, only Domain Admins can set Fine Grained Password Policies, but you can delegate these rights.
One of the possible implementations of multiple password policies is setting a different password policy to administrative accounts (IT Staff who is managing AD, or have other elevated permissions, including the Domain administrator account (SID 500), with more restrictive policy settings, and setting another password policy for system accounts (used for example to run services)
This is how it works: http://technet2.microsoft.com/windowsserver2008/en/library/056a73ef-5c9e-44d7-acc1-4f0bade6cd751033.mspx?mfr=true
Configuring a PSO is easy : Open the Fine Grained Password Policy MMC GUI…. just kidding :-) Microsoft has not built a nice wizard or GUI around this, so you’ll have to do this the hard way. Luckily, Microsoft has done an excellent job in documenting most of the Windows configuration steps over the last couple of years, so Technet contains detailed information on how to set this up. You can visit http://technet2.microsoft.com/windowsserver2008/en/library/1e1c9618-cda9-489b-a1cb-bbc182216aee1033.mspx?mfr=true or http://blogs.dirteam.com/blogs/jorge/archive/2007/08/09/windows-server-2008-fine-grained-password-policies.aspx for more information on how to set up the PSO. Furthermore, some clever individuals decided to wrap a GUI around the process. One of the really excellent (and free) tools that can be used to manage the PSOs (using Powershell components) can be found at http://dmitrysotnikov.wordpress.com/2007/06/19/free-ui-console-for-fine-grained-password-policies/
Password policy settings :
For administrators, a min. password length of 12 characters should not be a big problem, or if you want to keep the passwords shorter, then at least consider setting the password expiry to 2 weeks.
For service accounts it may be hard to change passwords all the time, so setting no password expiration may be acceptable in certain scenario’s, but the password length should be something like 30 or 40 characters
Modifying the WSSG EC Domain Controller Baseline Policy
The second GPOAccelerator-created GPO I am going to review is the one that can be applied to Domain Controllers. This GPO is quite detailed and configures a lot of settings compared to the Default DC policy in Windows.
However, the following settings should be changed (these could be settings that are already configured to something else, or could be settings that have not been configured yet, and should be set in addition to the already existing settings) :
Policies – Windows Settings – Security Settings – Local Policies
Audit Policy
The WSSG EC Policy will only log the success events. In certain cases, logging the failure events as well can help you troubleshooting as well as tracing back attempts to access data/objects by unauthorized users.
I would at least consider auditing success AND failure events for
Audit account logon events
Audit account management
Audit directory service access
Audit logon events
Audit object access
These settings can be found under “Computer Configuration – Policies – Windows Settings – Security Settings – Local Policies – Audit Policy”
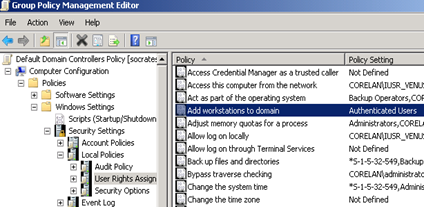
User Rights Assignments
Access this computer from the network
The WSSG EC Policy changes the default settings (which are indeed way to broad) to BUILTIN\Administrators, NT AUTHORITY\Authenticated Users, NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS
THis is a lot better already, however I don’t like “Authenticated Users” It would be better to create a Group in AD, add all of your known users into that group, and replace Authenticated Users with your own group. That way, you are sure that someone who is able to create a user account (in any way), cannot necessarily access your DC’s from the network.
Add workstations to the domain
Typically, you’d only want your IT staff to be able to add computers to the domain. In order to really be able to delegate and secure this kind of activity, there are 2 places that need some configuration
1. Edit the GPO that is applied to your DC’s – Go to “Computer Configuration – Policies – Windows Settings – Security Settings – User Rights Assignments
Edit “Add workstations to the domain”, remove “Authenticated Users” (Default Policy) or “BUILTIN\Administrators” (WSSG EC Policy) and add your IT Staff users. If changing this setting breaks your attempt to add a new DC to the Domain, you may have to add your Domain Admins/Enterprise Admins group as well)
2. Open Active Directory Users & Computers. Go to View and enable “Advanced Features”. Right-click “Computers” and go the the Security tab. Make sure regular users (Authenticated Users, etc) have read-only rights. You don’t need to add your IT Staff to the ACL. After all, it would be much better to create a separate OU structure, grant access to that OU, and set necessary permissions to the OU to the IT Staff. This way they can pre-create the computer objects before adding a computer to the domain. That is, imho, the best way to manage your computer objects (or at least the addition of computer objects in your environment)
Log on locally
Change this setting from “Not defined” to your local admin group, Domain Admins, BUILTIN\Administrators… whatever, as long as you don’t allow regular users to log on locally on a DC. In most cases, BUILTIN\Administrators will do just fine. If you’re not an admin, there’s nothing you should do on a DC.
Backup files & directories, Restore files & directories
By default, this setting is set to “not defined”. I would suggest changing this to your admin groups, BUILTIN\Administrators and BUILTIN\Backup Operators
Change the system time
Set this parameter to your admin group, BUILTIN\Administrators and LOCAL SERVICE
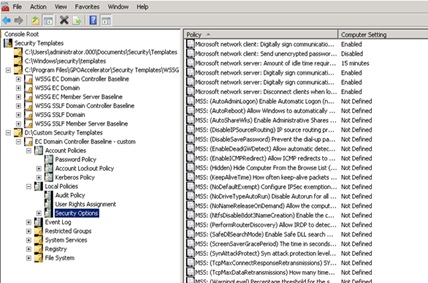
Security Options
DCOM: Machine Launch Restrictions in Security …
set to “configured”
Add your IT admins group and grant permissions for “Remote Activation”
This setting is required to allow IT admins to perform Group Policy Modelling, on Windows 2003 server SP1 or higher (http://support.microsoft.com/?kbid=914047)
Interactive Logon
Display user information when the session is locked : set to Do Not Display User Information
Message text for users attempting to log on : enable and enter a security banner. Do NOT include wording/verbiage such as “Welcome to the server”, or “Welcome to the domain” or something like that. Be very specific in your statement. Example text could be
This system is restricted to authorized users. Individuals attempting to gain unauthorized access to this system will be prosecuted. If you are unauthorized, terminate access right now. Clicking on OK indicates your acceptance of the information in the message above.
Message title for users attempting to log on : enable and enter a Message Title. Example : “it is a criminal offense to continue without proper authorization”
Network Security
Force logoff when logon hours expire : Set to enabled
Shutdown
Clear virtual memory pagefile : set to Enabled
Modifying the WSSG EC Member Server Baseline Policy
You can use the WSSG EC Member server baseline policy to apply a good security baseline to all of your servers (non DC’s). Some of the settings above will apply to these servers.
I would recommend setting a GPO before configuring other roles. You can also apply some of the custom TCP/IP settings that can be found near the bottom of this post to all of your servers, so don’t forget about these. Next, configure roles/features, install applications. and finally, run a SCW before you put the machine in production.
Update the SCE database and apply a MSS Security Template to get more options in your GPO
Earlier in this post, I talked about a third option in the GUI wizard : “Update SCE”.
Before you will be able to see the MSS specific settings in the GPO editor (SCE), you need to extend the SCE database, and then import a Security Template that contains these MSS settings. Running “Update SCE” will not add any settings to your GPOs, it will only make sure that you will be able to see the new settings when you import one of the MSS Security Templates (that are made available as part of GPOAccelerator)
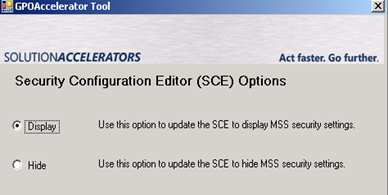
Launch the GPOAccelerator GUI again and click the “Update SCE” button this time
Choose to “Display” the SCE Options
click continue and accept the warning, and wait until the process finished. You will now be able to edit the Security Templates (.inf files)
Note : You can also extend the SCE from Command Line : cscript GPOAccelerator.wsf /ConfigSCE or remove the settings again using cscript GPOAccelerator.wsf /ResetSCE
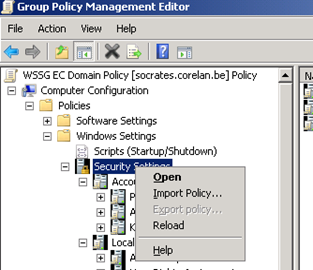
You are now ready to import the MSS specific settings into your GPO : Open Group Policy Management Console, edit your GPO, Open “Computer Configuration – Policies – Windows Settings – Security Settings”, right click and choose “Import policy”
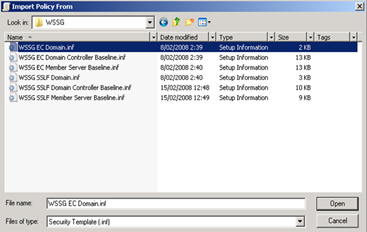
Navigate to C:\Program Files\GPOAccelerator\Security Templates\WSSG and select the Template that applies to this GPO. In my example, I have edited the Domain Policy, so I’ll select the WSSG EC Domain.inf file (You should do the same for your DC and member server GPO’s as well)
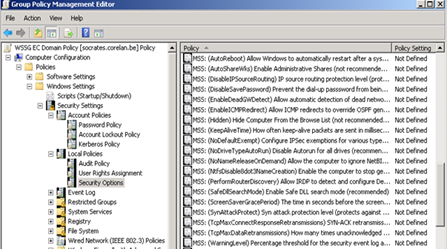
If you now open for example Security Options under “Computer Configuration – Policies – Windows Settings – Security Settings – Local Policies”, you’ll see the MSS: specific settings.
Further hardening regular (EC) servers using MSS extensions
I would recommend using the following MSS specific settings in a GPO that applies to all of your servers (including Domain Controllers):
AutoAdminLogon : disabled
DisableIPSourceRouting : enabled
NoDriveTypeAutoRun : disabled
NoNameReleaseOnDemand : enabled
Further hardening some (EC) servers using MSS extensions
The following settings should be applied to all servers whenever possible (Test these settings because they might impact the operation of your server) :
AutoShareWks : disabled
Hidden : enabled
Security Configuration Wizard : role based Firewall rulesets, Services modifications, Registry Security and Auditing
Windows 2008 is very much role based. The Security Configuration Wizard will attempt to identify the roles that are installed on a server, and change Firewall rules according to the roles that it has found on the system. The built-in roles can be hardened using built-in SCW templates (xml files), but you can add other templates as well (e.g. for MS Exchange 2007 roles : http://technet.microsoft.com/en-us/library/aa998208(EXCHG.80).aspx and http://technet.microsoft.com/en-us/library/bb124977(EXCHG.80).aspx)
Basically, these templates link the roles & features to network ports, so the firewall ruleset can be adjusted accordingly, based on the roles that are installed on a given 2008 Server.
The SCW wizard is pretty much self-explanatory, however the key component is veryfying that the correct roles have been identified. Otherwise, you’ll end up with a broken system.
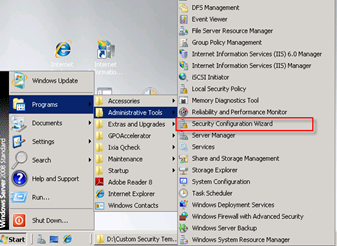
Launch the SCW Wizard from Start – Programs – Administrative Tools
Accept the welcome text
Select “Create a new security policy”
You can create a new policy for this server, or get the running configuration from another (similar) server. So if you get the config right for for example a DC, you can use this config for the other DC’s as well. This “copy” is one time, so if you change the config on the source DC, it will not be changed on the current machine, unless you run SCW again.
After the security database has been processed, click the ‘view configuration database’ button
This option will show you the roles/features/apps that have been discovered and enumerated on the system.
Close this screen and click next to continue
First, you’ll enter the Role-Based Service Configuration
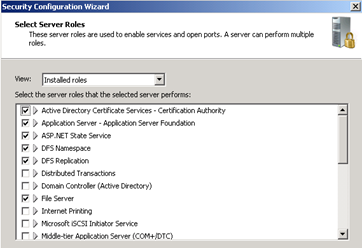
Set the scope to “Installed roles” and review whether the roles that were discovered match with what is installed on the system
Do the same for Features (Installed Features) and Options (Installed Options)
Next, review the page that lists the additional applications
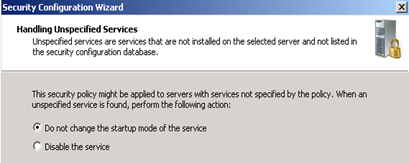
Next, Choose what you want the wizard to do with unexpected services :
Review the changes that will be applied to services
The next section “Network Security” will change the Firewall rulesets. Review the list of rules and click next
The next section will change Registry settings :
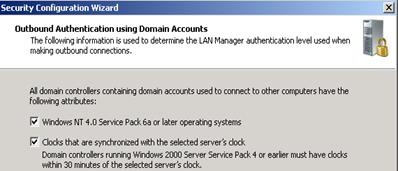
(note that this last option impacts the max clock skew – it is set to 5 minutes using the DC GPO, so I’d suggest thinking about keeping all clocks in sync, no matter what)
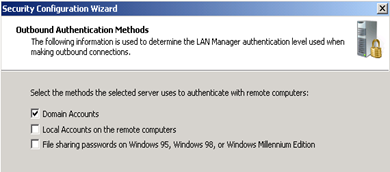
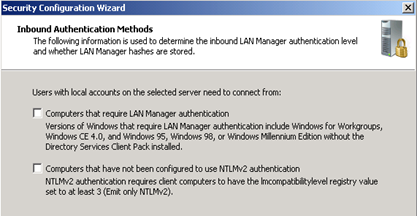
Change the inbound authentication methods if you environment supports this
Review the registry changes summary
Make changes for the audit policy. You can set these settings via a GPO as well, so you can skip this setting and configure auditing elsewhere
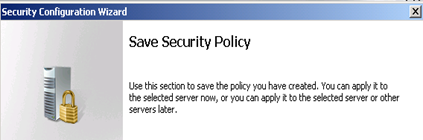
Save the policy
Pick a name (so you can find the policy back later on) and save the policy. The result is an xml file that can be modified manually if you want to.
You now have the option to apply the policy now or later. If you apply the policy, you’ll need to reboot the server
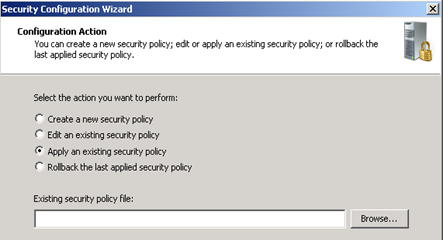
You can apply a saved policy by running the SCW wizard again and select to apply an existing policy
It is highly recommended to run this SCW on every server – DC’s, member servers, bastion hosts….
More information about the Security Configuration Wizard can be found at http://www.microsoft.com/downloads/details.aspx?FamilyID=903fd496-9eb9-4a45-aa00-3f2f20fd6171&displaylang=en
SSLF High Security Servers (Standalone servers with specific roles and an elevated security exposure level)
I’m not going to discuss the settings for the SSLF GPO right now – this GPO/Security Template requires extensive testing. It is easy to break stuff with this set of configuration parameters, so you’ll have to tweak them a bit.
Working with custom Security Templates
Definitions
A GPO contains of a set of registry settings. The GPO editor (SCE) is in fact nothing more than a GUI wrapped around these settings, allowing you to change the values of these registry settings before deploying them to one or more systems/users
A Security Template (.inf) is a set of pre-defined settings and values that can be applied to a server, via a GPO. The combination of a GPO and a Security Template allows you to quickly create GPO’s including the necessary customizations.
If you open a Security Template file, you’ll see something like this (I’ve taken the WSSG EC Domain.inf file from GPOAccelerator as an example) :
| ; (c) Microsoft Corporation 2008 ; ; Security Configuration Template for Security Configuration Editor ; ; Template Name: WSSG EC Domain.inf ; Template Version: 1.0 ; ;This Security Configuration Template provides settings to support the ;EC Domain settings for the Windows Server 2008 Security Guide. ;Please read the entire guide before using this template. ; ; Release History ; 0001 – Original February 27, 2008 [Unicode] Unicode=yes [Version] signature=”$CHICAGO$” Revision=1 [System Access] MinimumPasswordAge = 1 MaximumPasswordAge = 90 MinimumPasswordLength = 8 PasswordComplexity = 1 PasswordHistorySize = 24 LockoutBadCount = 50 ResetLockoutCount = 15 LockoutDuration = 15 ClearTextPassword = 0 [Registry Values] [Profile Description] Description=This Security Configuration Template provides settings to support the Enterprise settings for the Windows Server 2008 Vista Security Guide. Please read the entire guide before using this template. |
You can find more ready-made Security Templates on each Windows server, or on specific servers, serving specific purposes such as securing Exchange server etc.
Just search for *.inf files (which may not all be Security Templates, but you’ll recognize a Security Template when you see one :) )
Custom – Security Templates
As you can see, these templates are just plain text files, but it might not be a good idea to edit these files using notepad. Furthermore, you may want to leave the default templates untouched, and create your own templates based upon a copy of the original files.
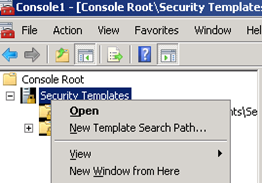
First, create a folder where you want to store your own templates. Make sure to change the NTFS permissions on this folder so only your admins can access this folder. Next, create a “Security Templates” MMC. Open the MMC, right click Security Templates and choose “New Template Search Path”.
Add your custom folder to the list.
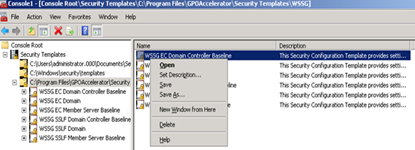
If you want to see the original/default templates, then add C:\Windows\Security\Templates to the list as well. You can create a copy of a Template by right-clicking on the Template and choosing “Save As”
As you can see, you can further refine the Security Templates before applying them to all of the relevant GPO’s in your environment.
Custom Settings
The following settings can be applied to any server. You can either change these parameters manually, use a script to deploy and apply a .reg file, or create a custom GPO (.adm(x)) and optionally a Security Template (.inf) and apply these custom registry settings using a GPO, Or alternatively, extend the SCE database and add your own registry keys :
http://support.microsoft.com/kb/214752
http://www.windowsdevcenter.com/pub/a/windows/2005/03/15/local_security_policies.html
Custom – TCP/IP Settings
General settings
Disable IP Source Routing : This feature is now turned off by default for IPv4 connections, but it is still active for IPv6 connections. Even if you are not planning on using IPv6 right now, it might still be a good idea, just in case you decide to start using it. You can disable IP Source Routing for IPv6 by changing the following registry key :
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters
DisableIPSourceRouting (Value Type : REG_DWORD)
Set to 1 or 2
Possible values : 0 = forward all packets, 1 = don’t forward source routed packets, 2 = drop all incoming source routed packets
Default values : 1 for IPv4, 0 for IPv6
If you want to verify the settings for IPv4, then check the value of DisableIPSourceRouting under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
Note : this setting can be set using a SCE Extended GPO (look for one of the MSS: specific settings under “Computer Configuration – Policies – Windows Settings – Security Settings – Local Policies – Security Options”)
Disable IP Routing : make sure IP routing is disabled, unless you want your server to act as a router. This setting is disabled by default under Windows 2008. Make sure IPEnableRouter is set to 0 under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
(Default value is 0. Possible values : 0 = disable IP routing, 1 = enable IP routing)
Disable ICMP Redirects : unless you have a very good reason to leave this functionality turned on, you should consider disabling this by changing the value of HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\EnableICMPRedirects (reg_dword) to 0
Per interface settings
Assuming that you know how to match a network interface with a GUID, you should consider setting the following options for each of the interfaces
Disable Perform Router Discovery : Set PerformRouterDiscovery (REG_DWORD) under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{interfaceGUID} to 0 (disabled)
Possible values are 0 = disabled, 1 = enabled, 2 = enabled only when DHCP “Perform Router Discovery” option is set. Default value is 2
Disable APIPA : For each adapter under HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\
{xxxxxxxxx} Replace this with the GUID of the adapters : Create a REG_DWORD called “IPAutoconfigurationEnabled” and set to 0x0
More information about these (and other registry settings for TCP/IP) can be found at http://www.microsoft.com/downloads/details.aspx?FamilyID=12ac9780-17b5-480c-aef7-5c0bde9060b0&DisplayLang=en
If you want more information about the netsh.exe command, visit http://go.microsoft.com/fwlink/?LinkId=49654
Custom – Other settings
Restrict access to Null sessions : Set HKLM/System/CurrentControlSet/Control/LSA/RestrictAnonymous to 1 on DC’s, and to 2 on other servers.
Disable Dial-Up Networking : Set (or create) HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\NetworkNoDialin (reg_dword) to 1
Disable File&Print sharing & close the associated open ports.
You can use firewall rules to do this, but in general, this may help as well :
Disable file & print sharing
Disable Netbios TCP/IP Helper Service
Disable Netbios over TCP/IP
Disable LMHOSTS Lookup
Disable the Computer Browser Service
Disable the Server service
Set SMBDeviceEnabled under HKLM\System\Controlset001\Services\NetBT\Parameters (Reg_Dword) to 0 to close SMB Port 445
Of course, don’t do this on DC’s or on File & Print Servers.
Delegation
DHCP
By default, only Enterprise admins have the ability to authorize DHCP servers.
You can change who can authorize a DHCP server by editing the ACL on the following service :
Go to the first DC in the forest, open Active Directory Sites and Services, and make sure “advanced features” is turned on (on Windows 2003) or enable “Show Services Node” on Windows 2008
Edit the properties of “NetServices” and go to ‘Security’
Add the group of admins you want to all to authorize DHCP servers
Give the group full control
Wait until replication has completed to all DC’s, and you should be fine.
GPO
After creating an admin group for AD administrators, you will need to grant access to this admin group so they can add GPO’s to the domain. Open the AD Users and Computers mmc, go to the “Users” folder, open the “Group Policy Creator Owners” group and add the AD Administrators group.
Additonally, make sure the AD Administrators group has RW access to the SYSVOL/
Additionally, open the GPMC, go to Forest:
Add rights to the Admin group to link GPO’s, do GPO modelling and analyse results
Next, select ‘Sites”, “show sites”, and add “Link GPO’s” Access to the sites that will be managed by this Admin group
Audit
Download MBSA (at time of writing, latest version is 2.1 beta 2) from http://www.microsoft.com/technet/security/tools/mbsa2_1/default.mspx#ETB and run scans against your systems. You should do this on a continuous basis and implement a process to review the delta’s between 2 scans
Additionally, implementing tools that will go through event logs (or even better, tools that will capture events before they are entered in the event log, such as OpsMgr) and look for specific codes will help you get (and hold) grip of your environment.
If I have some spare time, I might write some details on performing Security monitoring with OpsMgr 2007.
Downloads
I have modified the following Security Templates with most of the GPO settings that were discussed in this post.
After applying the template to your GPO’s, make sure to review the settings and to add any Domain Specific groups to these settings. (I had to leave them out as these groups are specific to my environment)
These templates do not contain the custom TCP/IP settings that are listed above, you’ll have to apply those settings manually.
You can download the modified Security Templates from the links below :
EC Domain Baseline modified template (1.3 KiB)EC Domain Controller Baseline modified template (14.7 KiB)
Don’t forget to extend the SCE using GPOAccelerator before you use these Templates !
© 2008 – 2021, Peter Van Eeckhoutte (corelanc0d3r). All rights reserved.
Similar/Related posts:
 Restoring 2003 AD Objects using Windows 2008 Server
Restoring 2003 AD Objects using Windows 2008 Server
 IPSec VPN between Windows Server 2008 and Juniper ScreenOS
IPSec VPN between Windows Server 2008 and Juniper ScreenOS
 Using Active Directory and IAS based Radius for Netscreen WebAuth authentication
Using Active Directory and IAS based Radius for Netscreen WebAuth authentication
 Free tool – PVE Active Directory Disable Users
Free tool – PVE Active Directory Disable Users
 Fixing ‘Compatibility Mode grayed out’ or ‘Unable to enable Run as administrator’ on Vista / Windows 2008 Server
Fixing ‘Compatibility Mode grayed out’ or ‘Unable to enable Run as administrator’ on Vista / Windows 2008 Server
6 Responses to Securing Windows Server 2008 and Active Directory
Corelan Training
Check out our schedules page here and sign up for one of our classes now!
Donate

Your donation will help funding server hosting.
Corelan Team Merchandise
Corelan on Slack
You can chat with us and our friends on our Slack workspace: